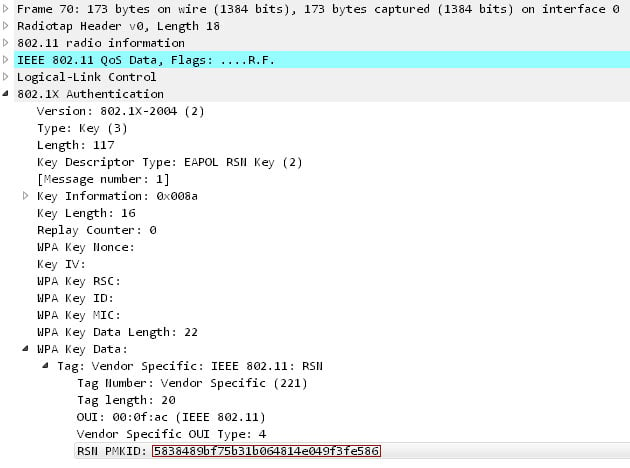
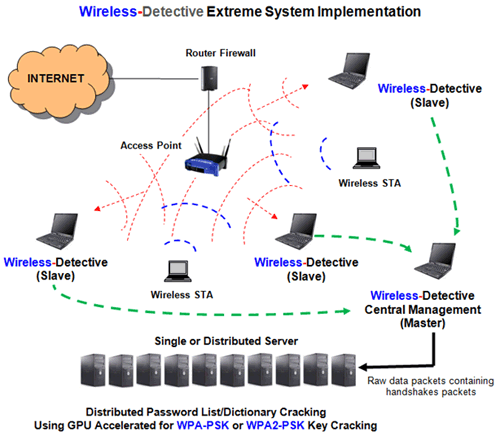
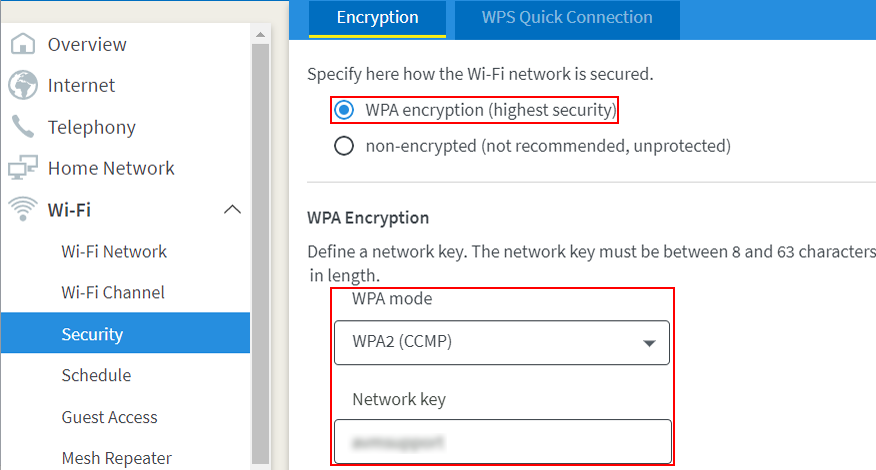
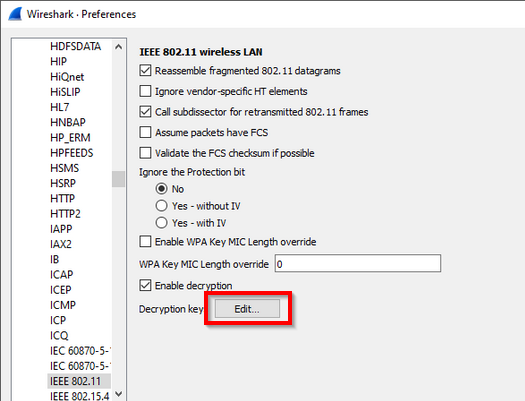
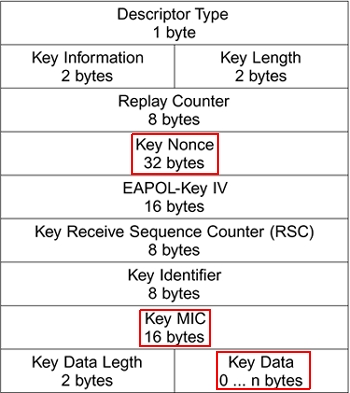
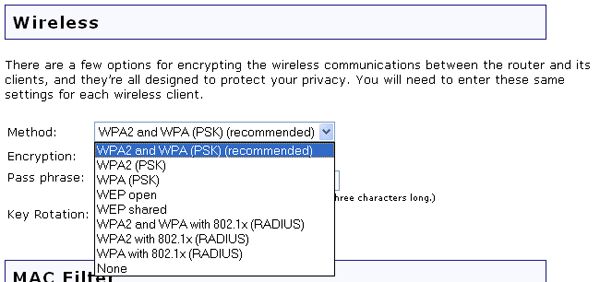
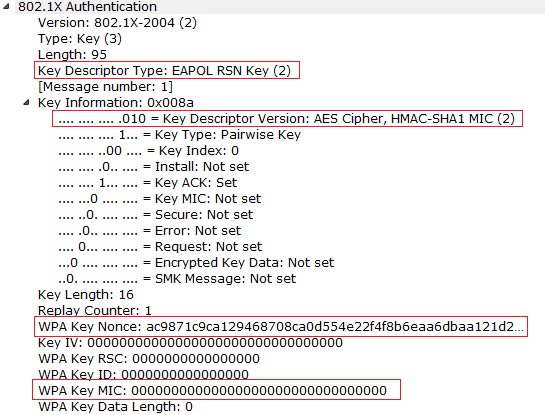
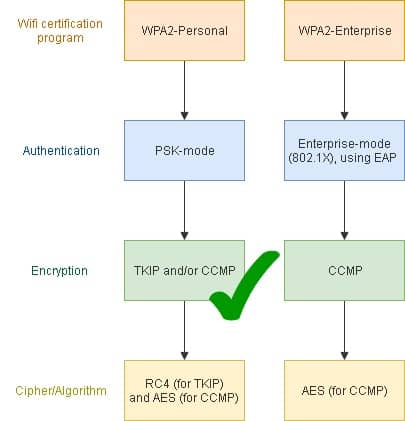
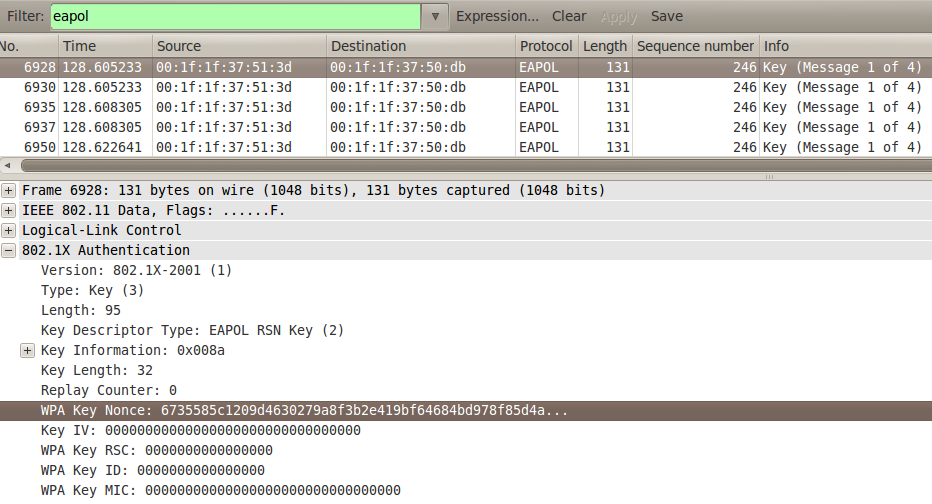
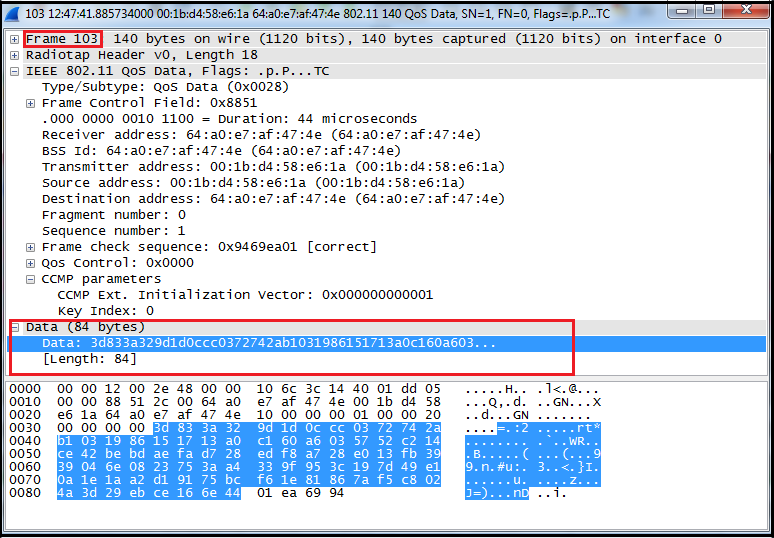
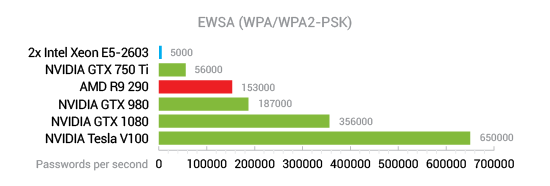
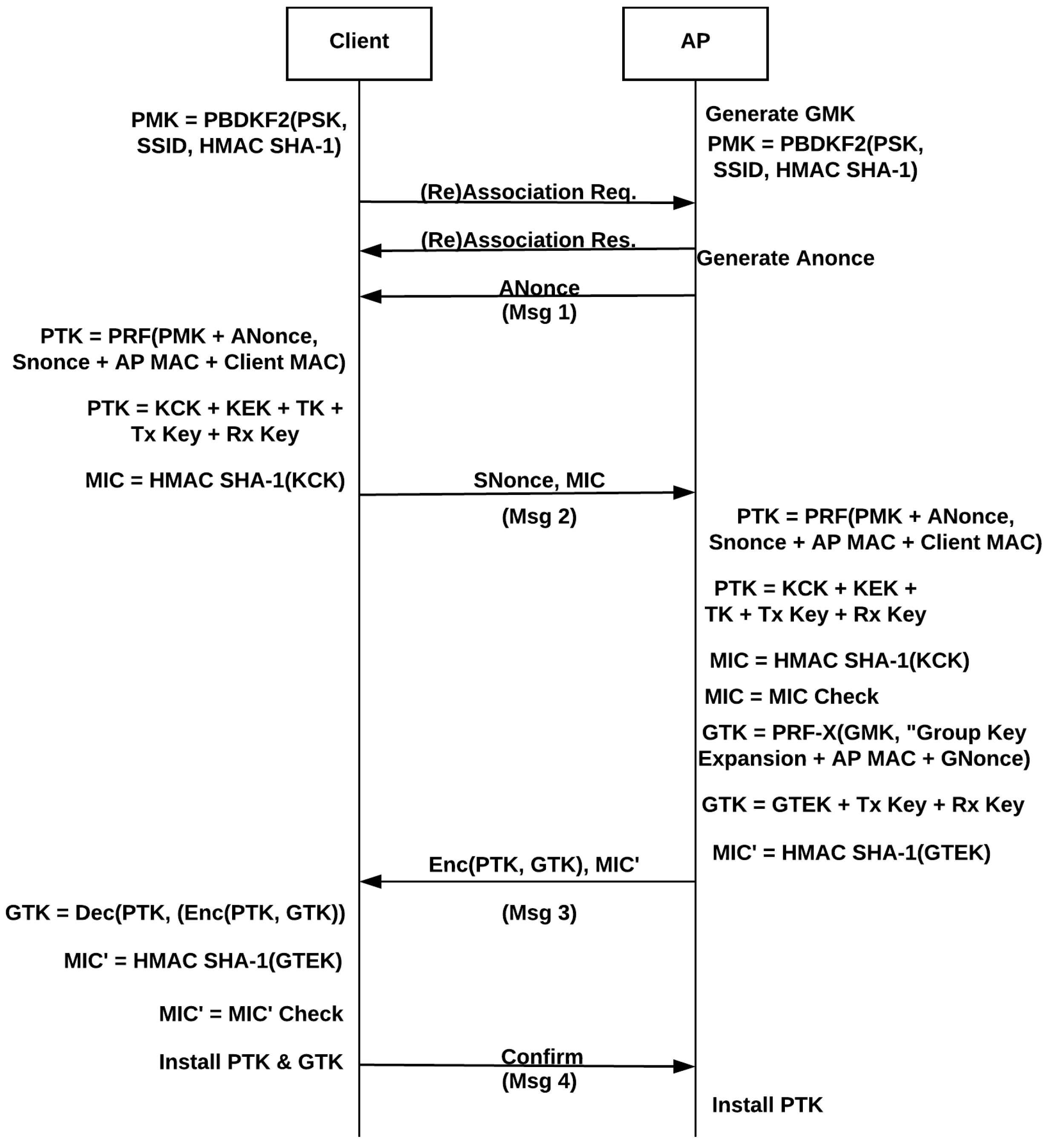
Running head: EXPLORATION OF PASSWORD LENGTH Page 1 Exploration of Password Length on Wireless Network Security James C. Duv
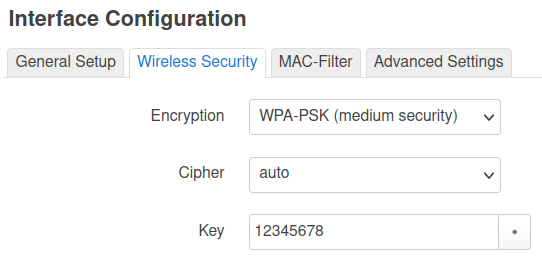
Why is WPA-PSK declared as "medium security" by openwrt despite any protocol using RC4 should be considered vulnerable? - Talk about Documentation - OpenWrt Forum
Electronics | Free Full-Text | A Comprehensive Attack Flow Model and Security Analysis for Wi-Fi and WPA3