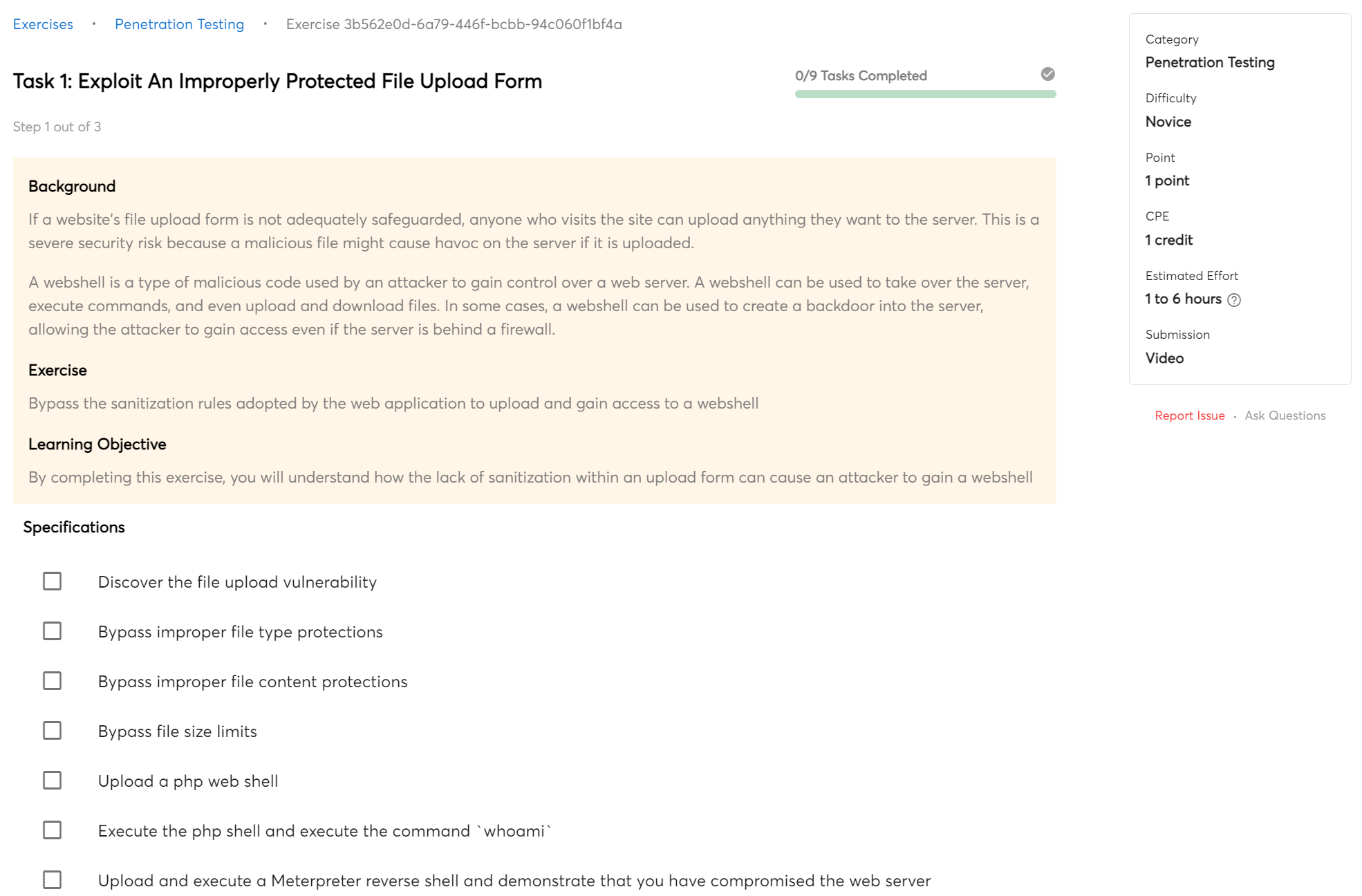
Cyber Attacks Explained - Web Exploitation - Cyber Security Blogs - Valency Networks - Best VAPT Penetration Testing Cyber Security Company - Pune Mumbai Hyderabad Delhi Bangalore Ahmedabad Kolkata India Dubai Bahrain

Web Application Security: Exploitation and Countermeasures for Modern Web Applications : Hoffman, Andrew: Amazon.de: Bücher
Computer Hacking Black Line Icon. Attempt To Exploit a Computer System or a Private Network Inside a Computer Stock Illustration - Illustration of color, loss: 176473964












![picoCTF — More Cookies [Web Exploitation] | by MR SHAN | Medium picoCTF — More Cookies [Web Exploitation] | by MR SHAN | Medium](https://miro.medium.com/v2/resize:fit:672/1*wxTxgkXE-9KjgQKf8GvhuA.png)