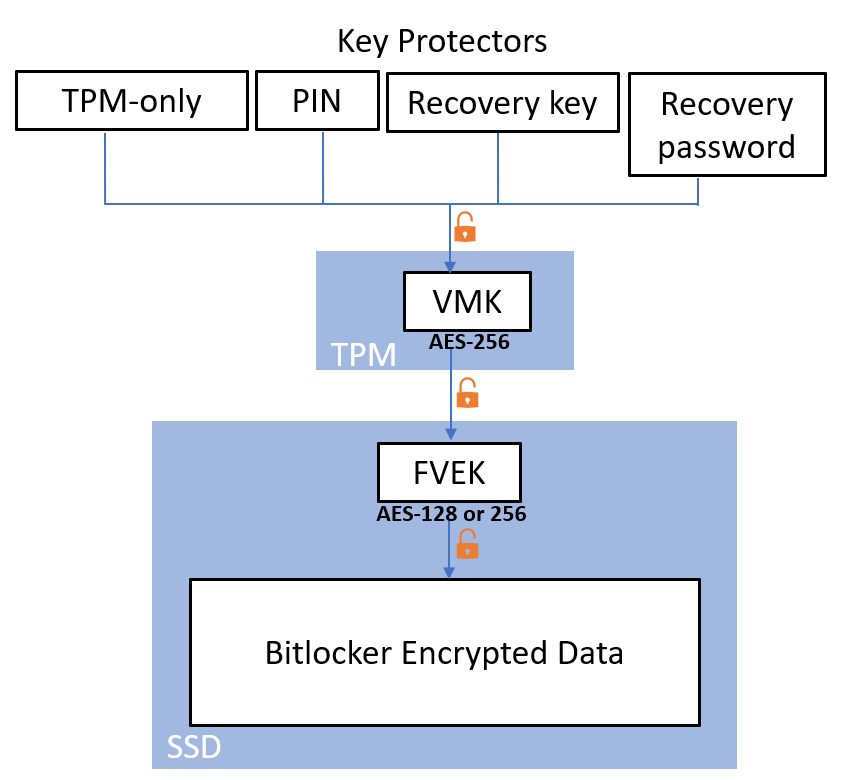
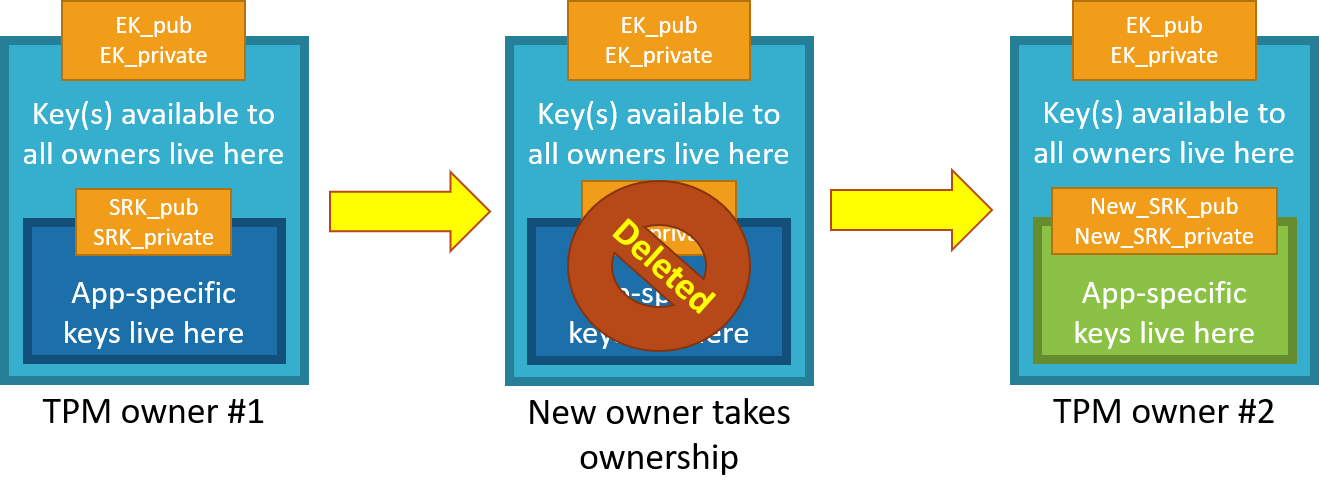
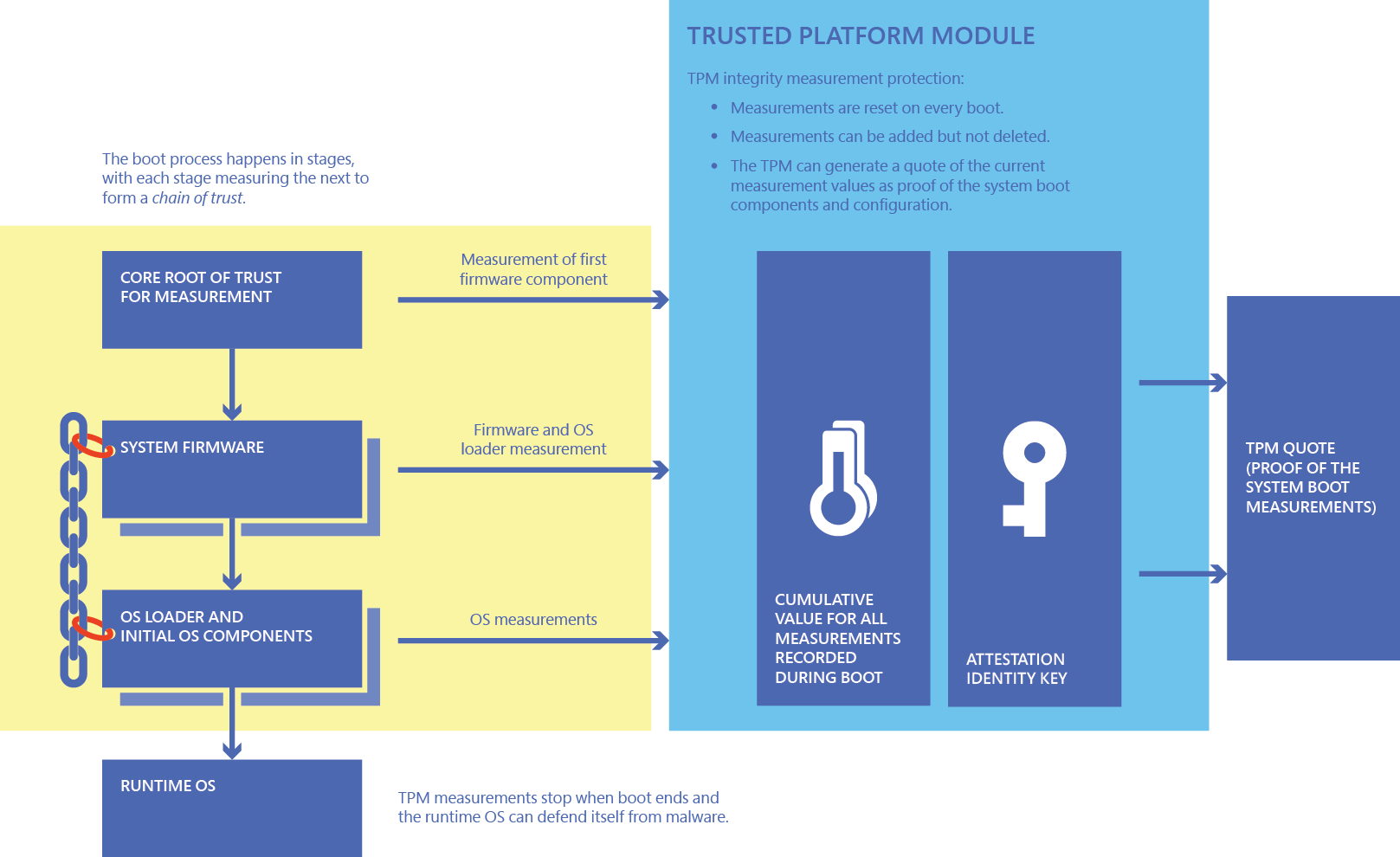
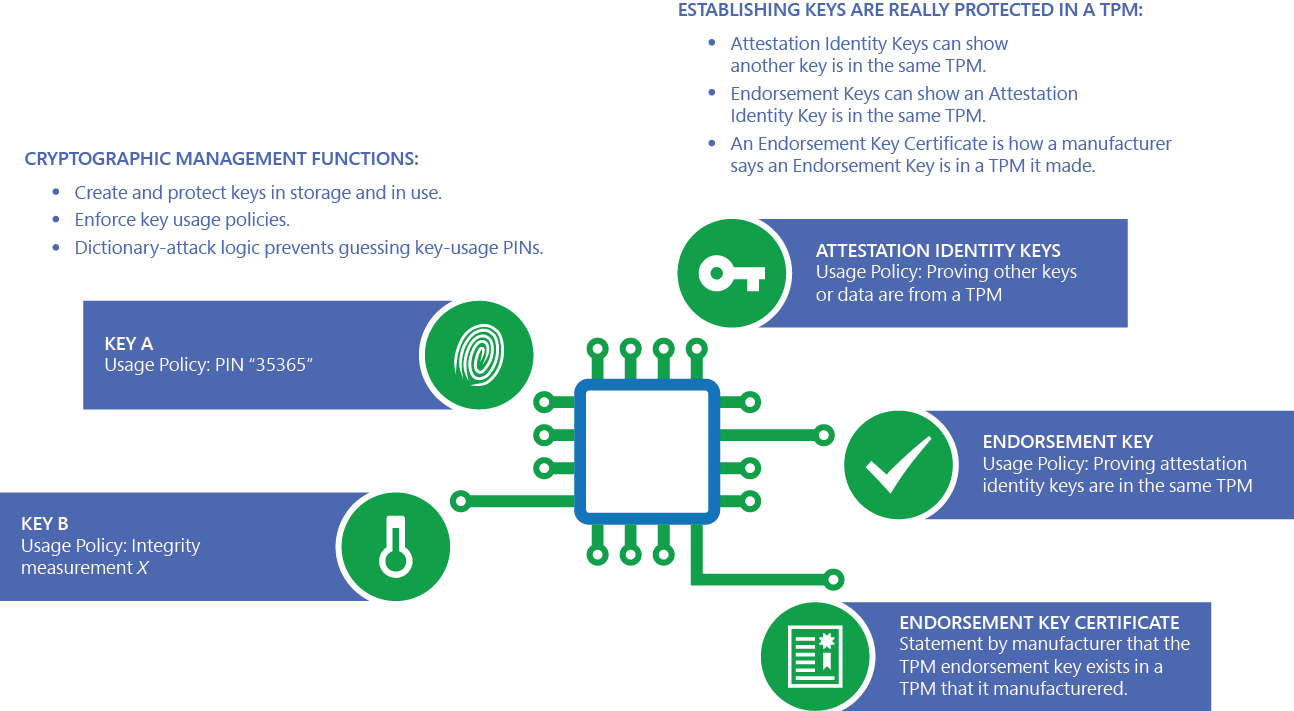
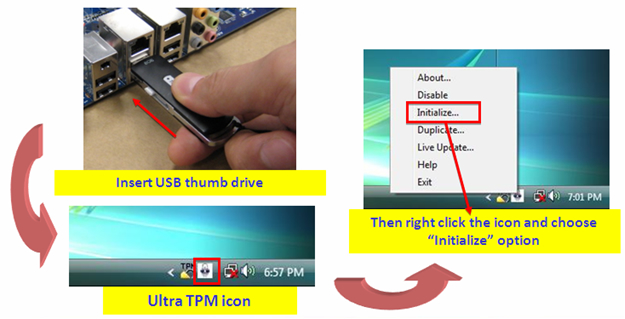
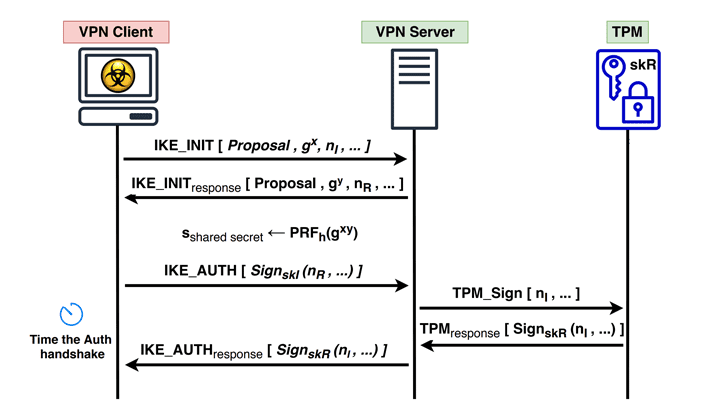
Data firewall trusted platform module (TPM) key tree. SRK: storage root... | Download Scientific Diagram
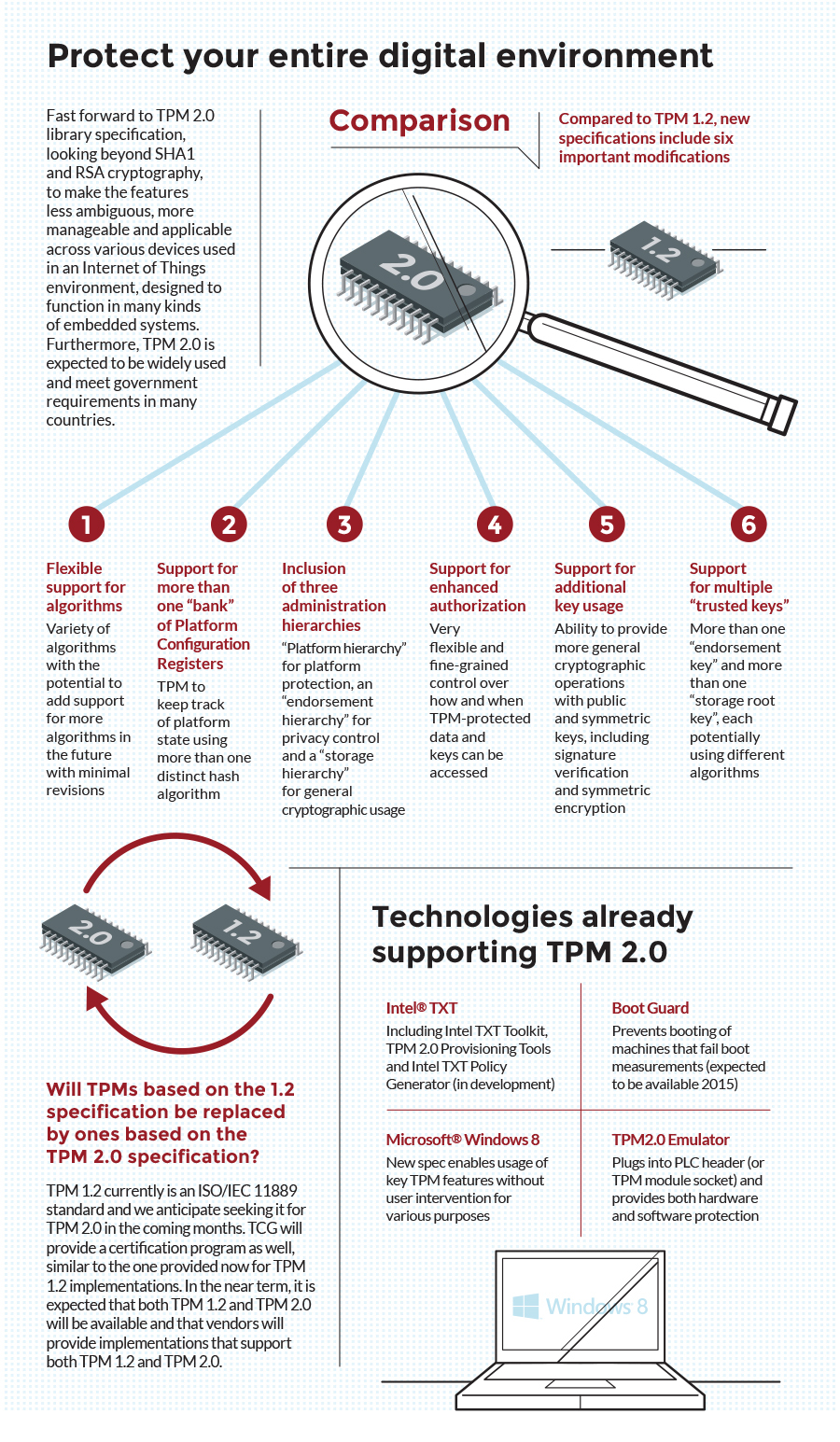
Trusted Computing Group lanciert TPM 2.0-Spezifikation für bessere Sicherheit von Plattformen und Geräten | Business Wire

Embedded World Product Showcase: Infineon Technologies OPTIGA TPM SLB 9672 - Embedded Computing Design

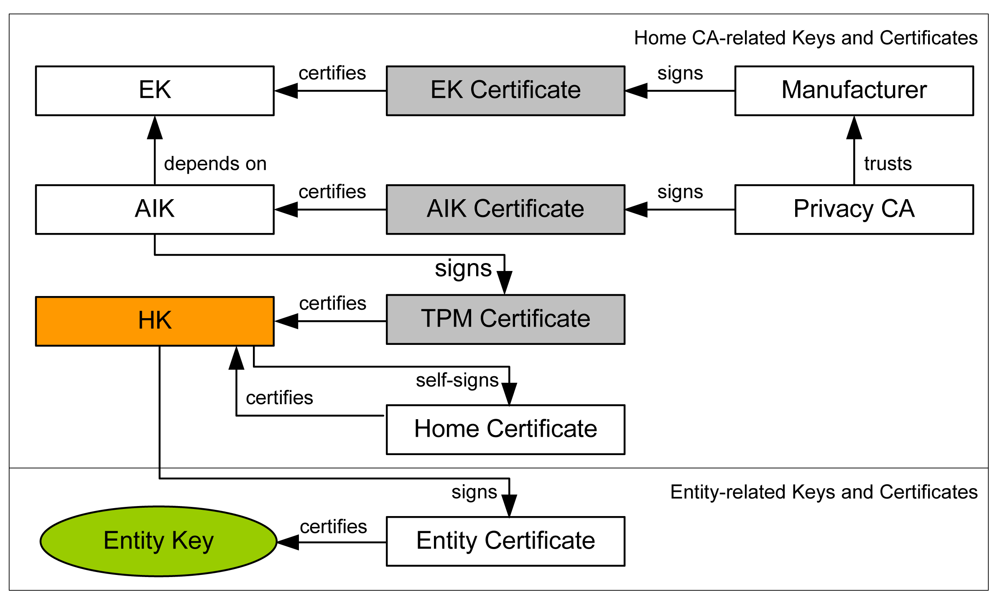
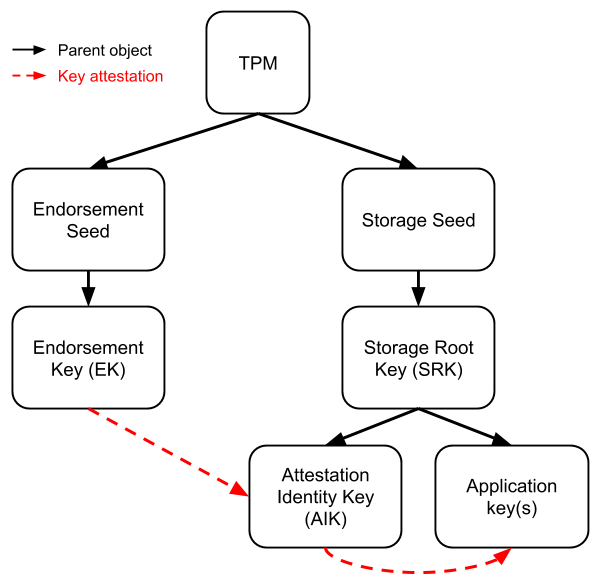
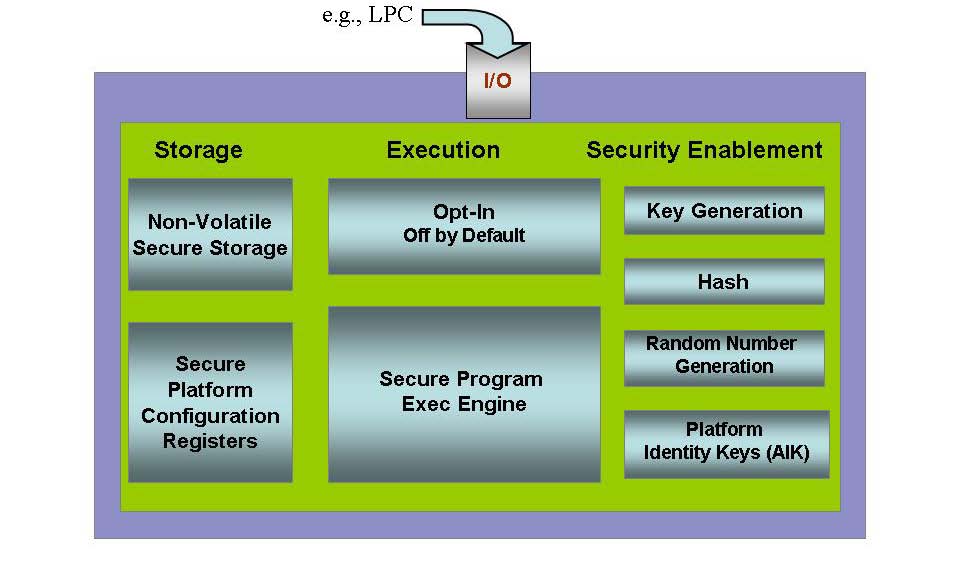
TKM Key Hierarchy Having in mind that TPM protected keys are bound to a... | Download Scientific Diagram