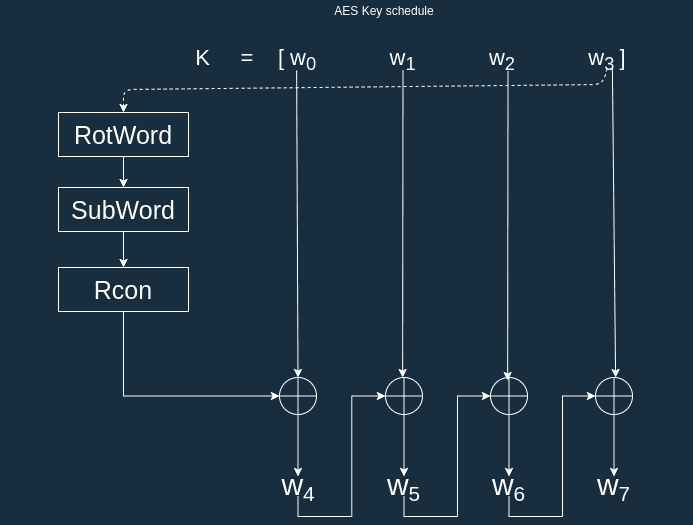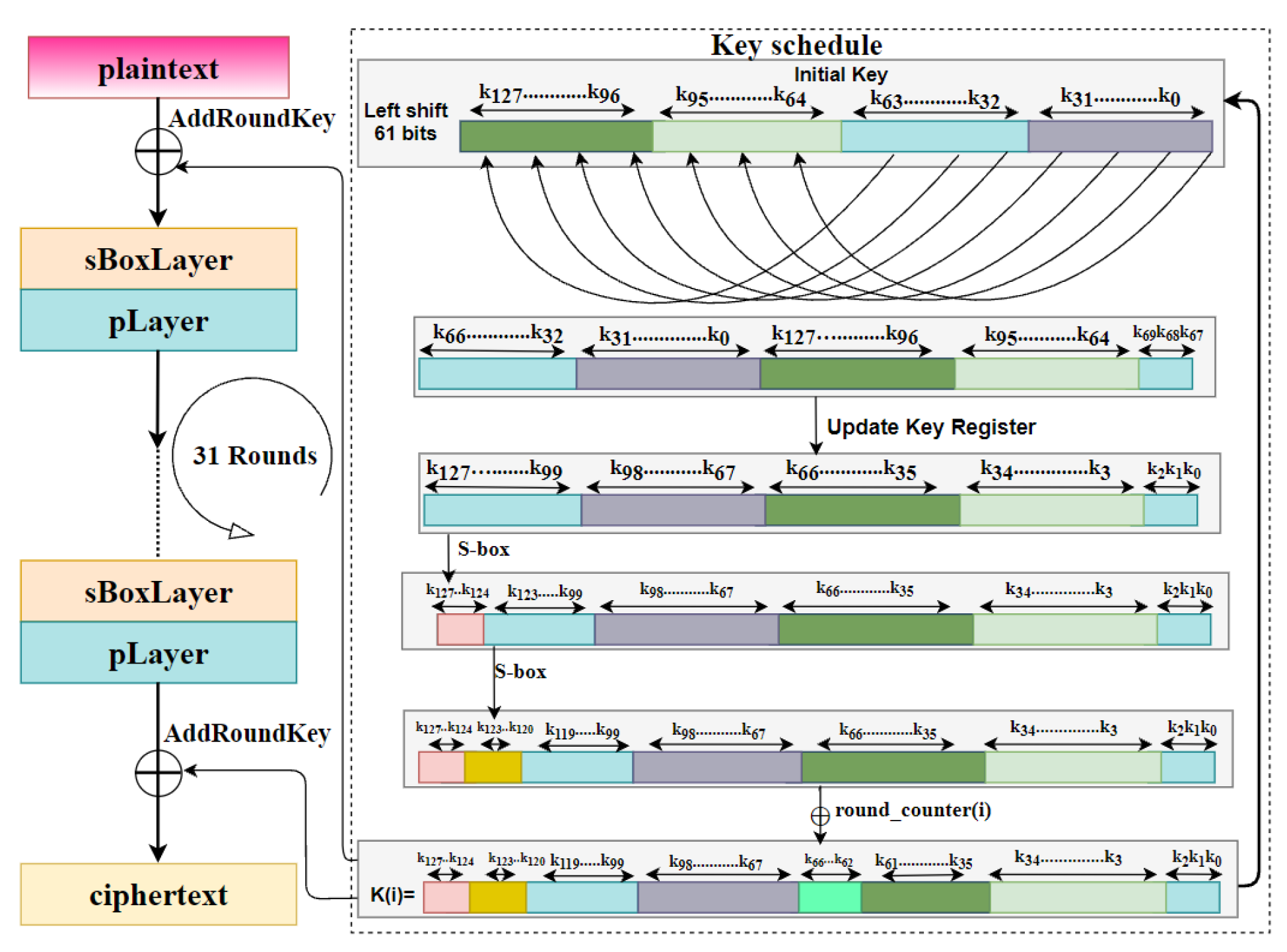
Symmetry | Free Full-Text | An Enhanced Key Schedule Algorithm of PRESENT-128 Block Cipher for Random and Non-Random Secret Keys

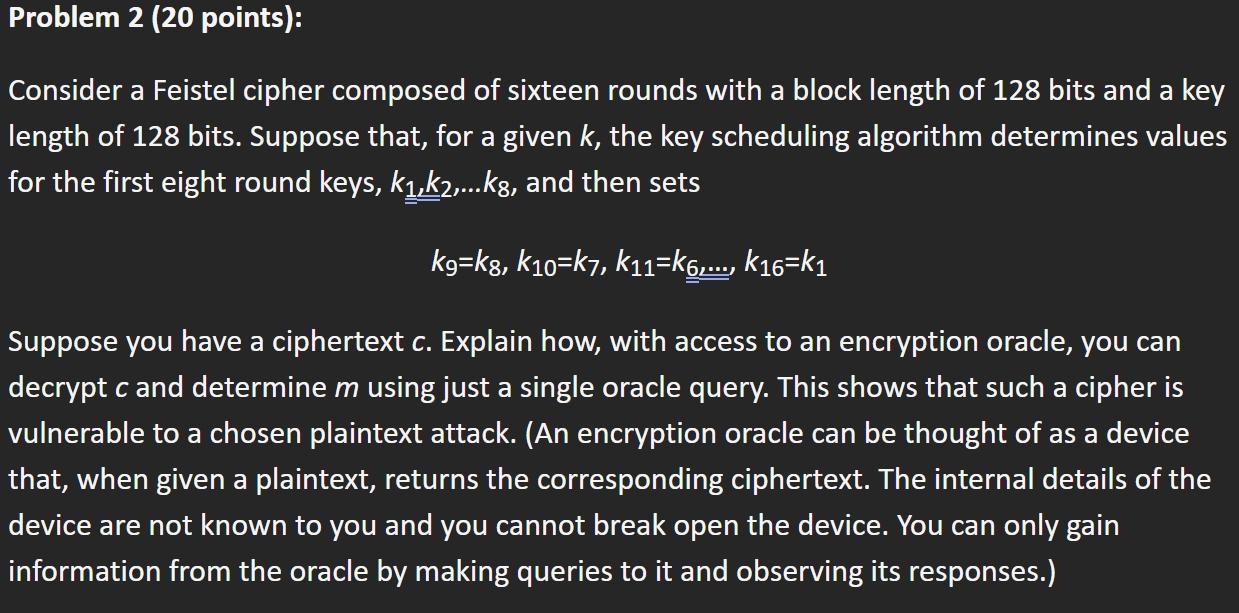
A Secure Key Scheduling Operation for International Data Encryption Algorithm using Serpent Key Schedule Operation | Semantic Scholar

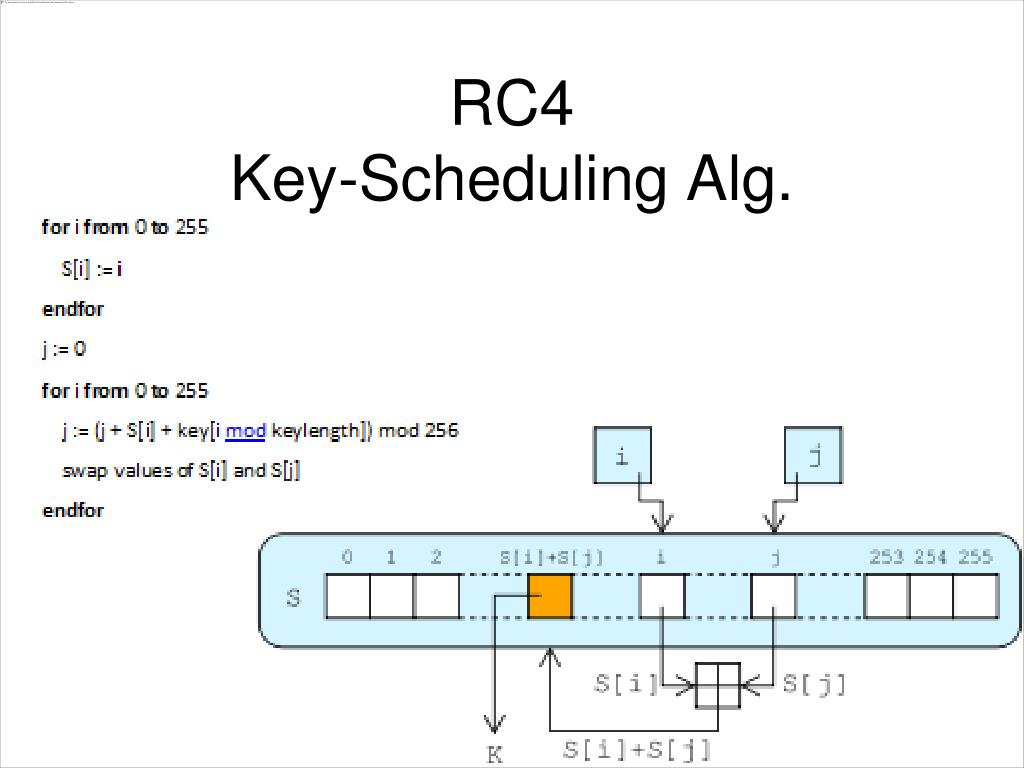
Vulnerability Testing on the Key Scheduling Algorithm of PRESENT Using Deep Learning | springerprofessional.de

GISKOP: A Modified Key Scheduling Operation of International Data Encryption Algorithm using Serpent Key Scheduling | Semantic Scholar