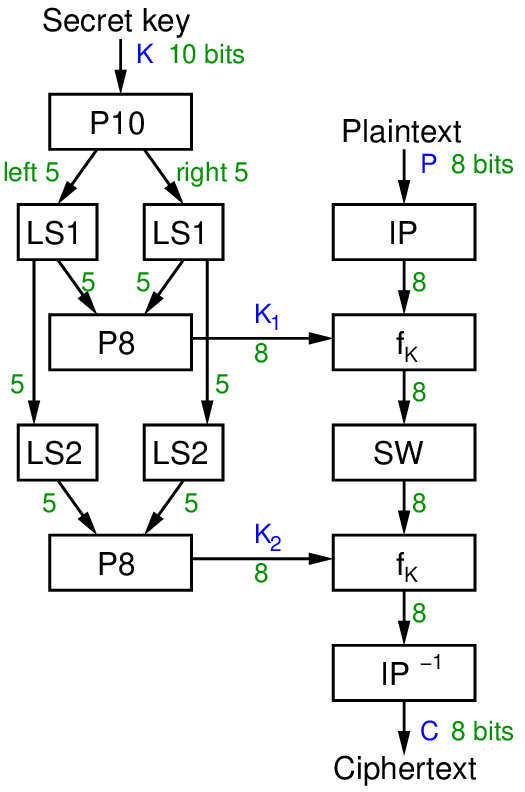
Generation of Cryptographic Keys from Personal Biometrics: An Illustration Based on Fingerprints | IntechOpen

Enhanced key-generation algorithm using MRMCTT in Data encryption standard algorithm | Semantic Scholar
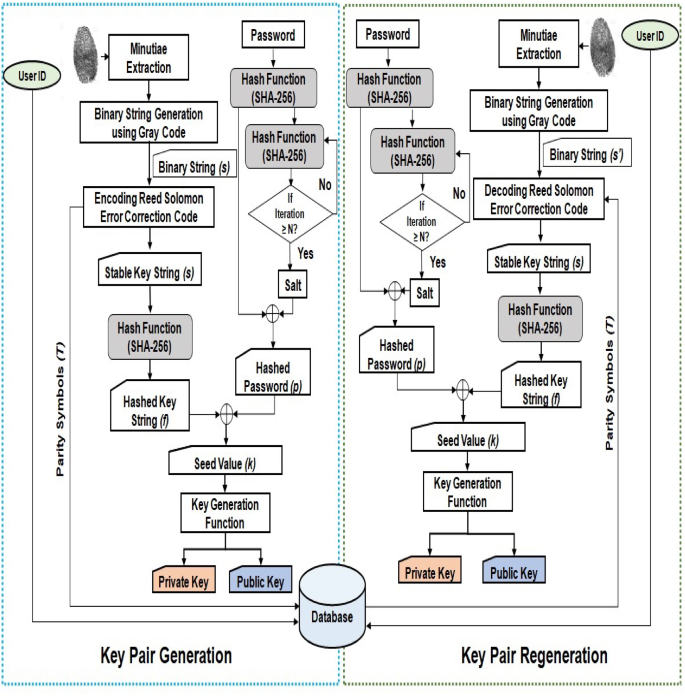
Two-factor-based RSA key generation from fingerprint biometrics and password for secure communication | SpringerLink
Database Key Generation in Java Applications | Down Home Country Coding With Scott Selikoff and Jeanne Boyarsky