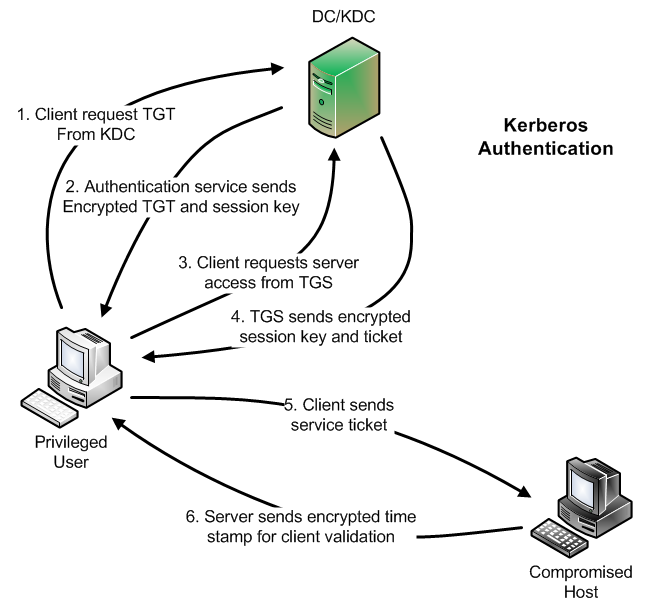
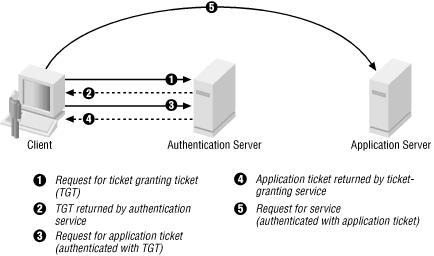
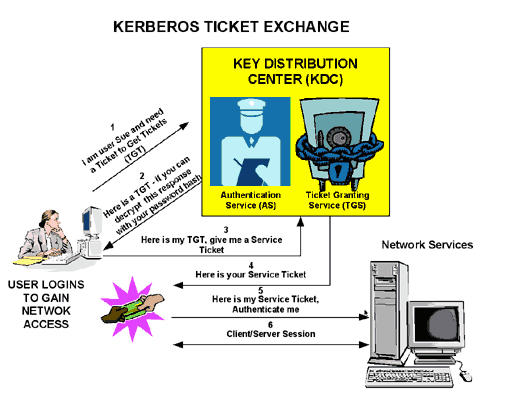
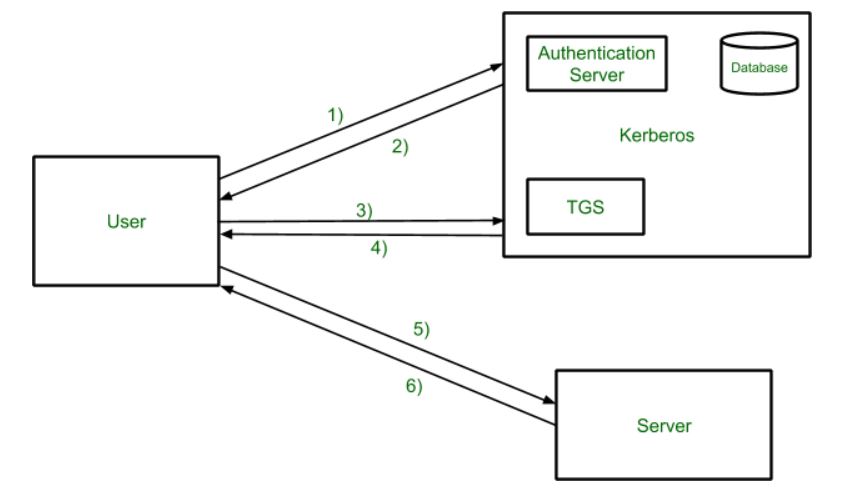
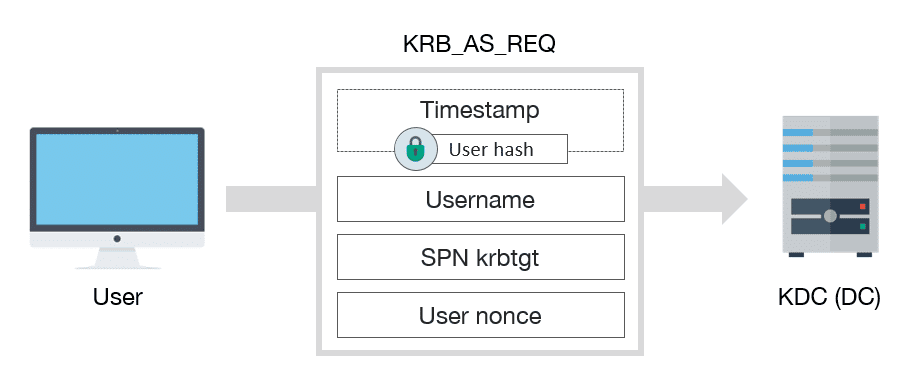
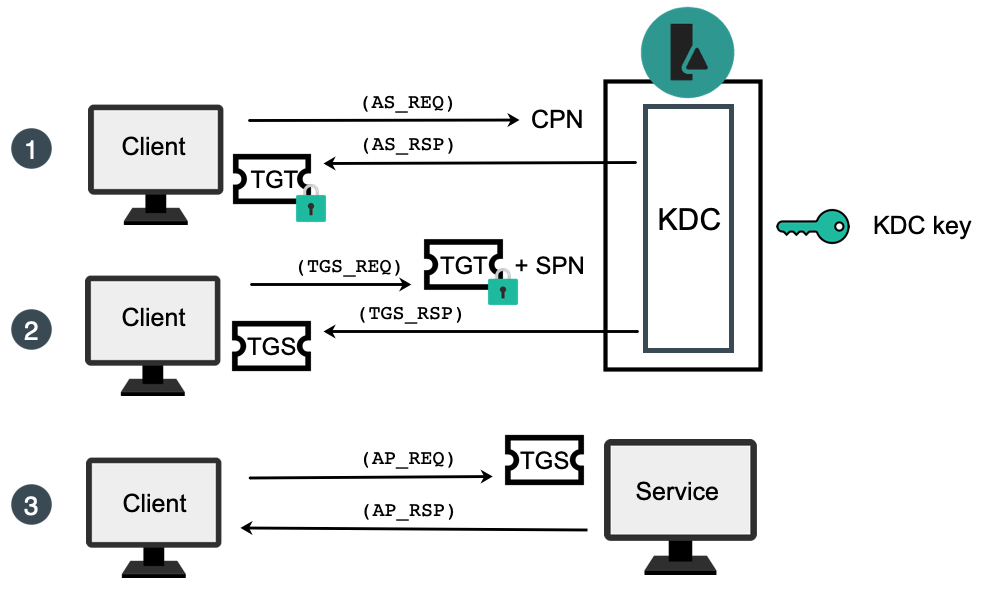
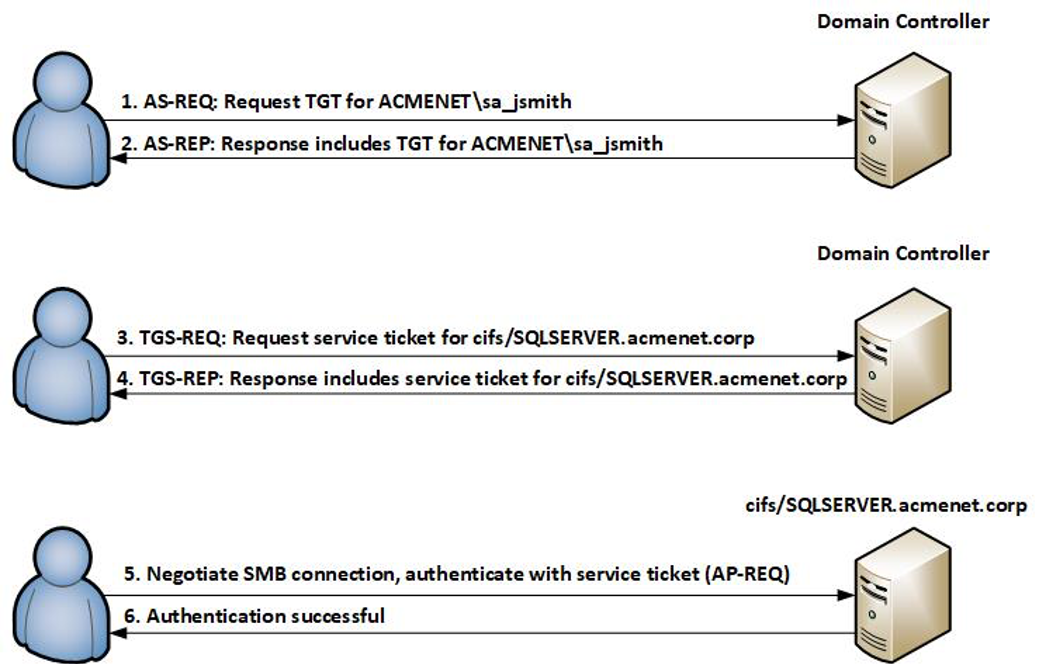
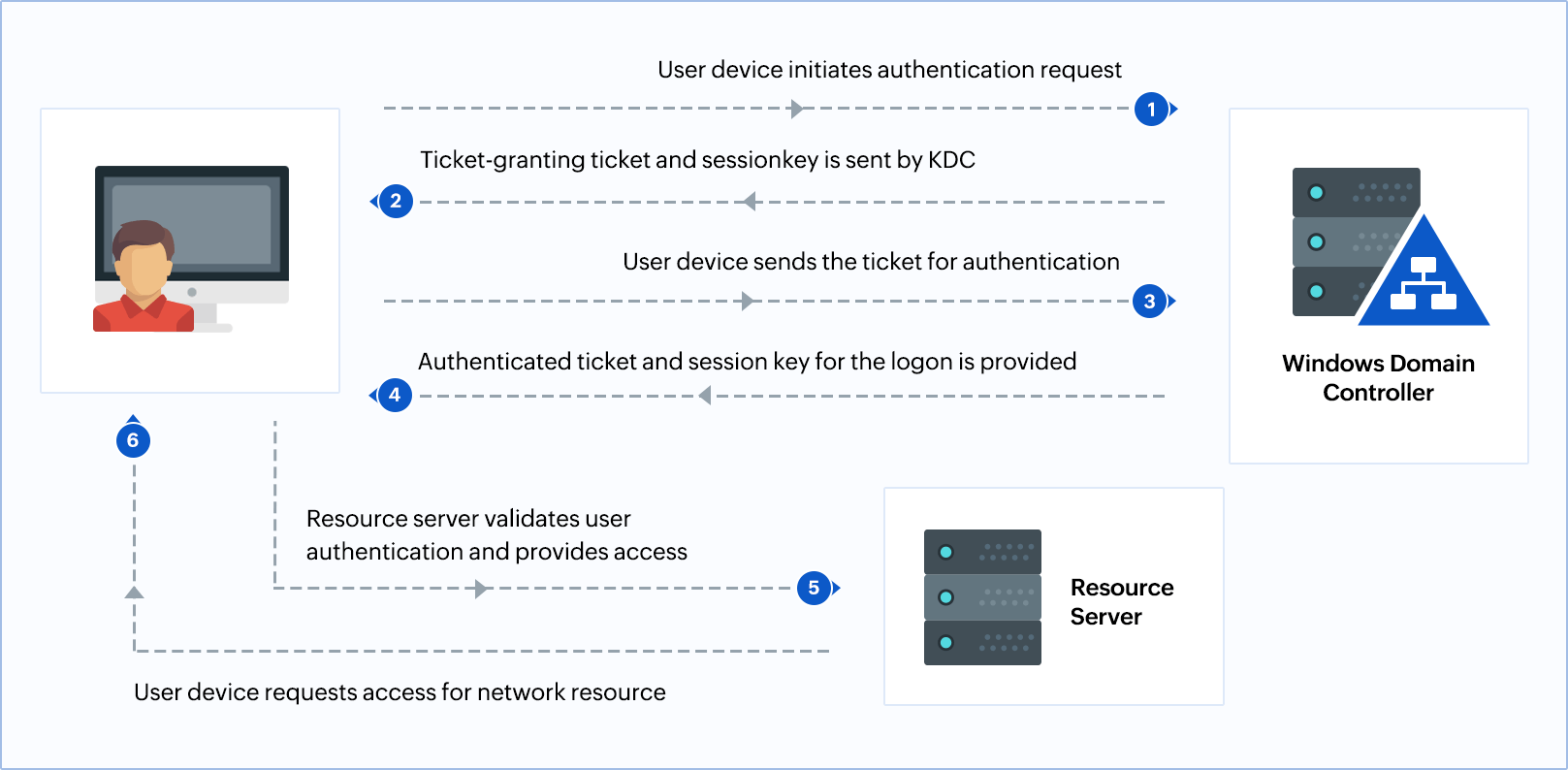
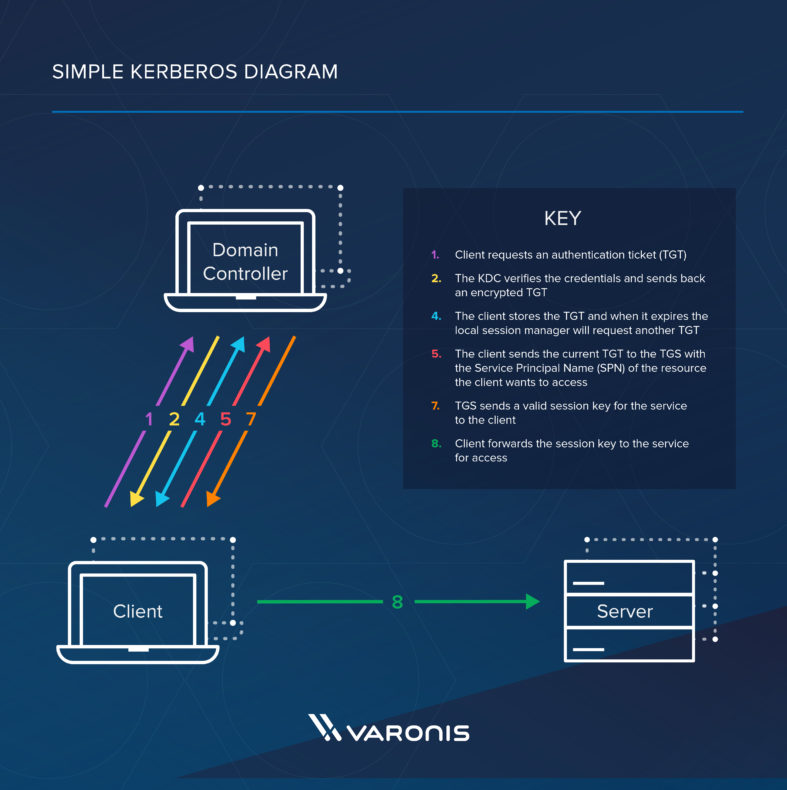
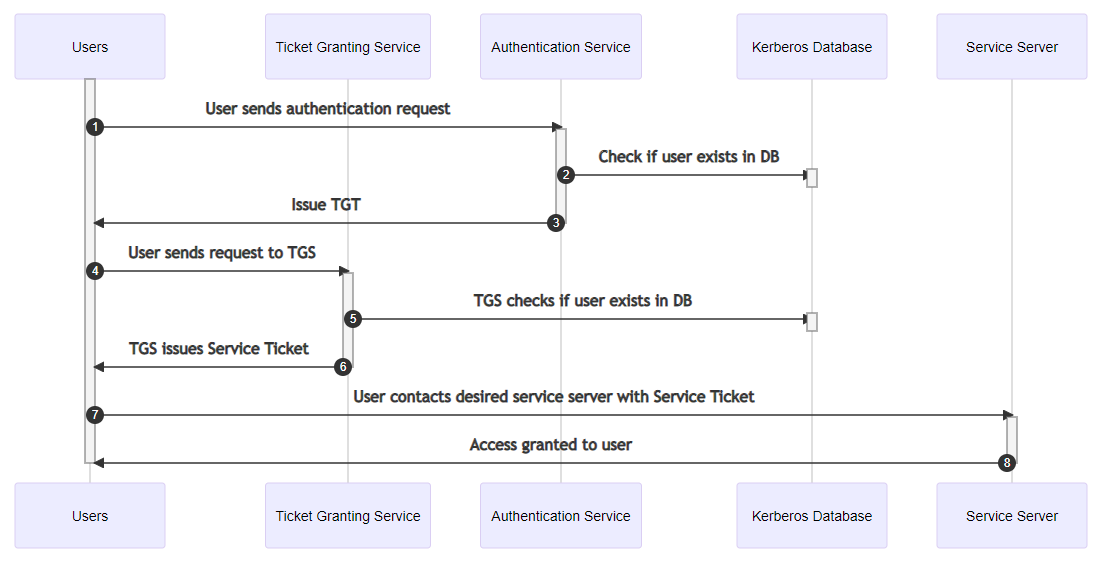
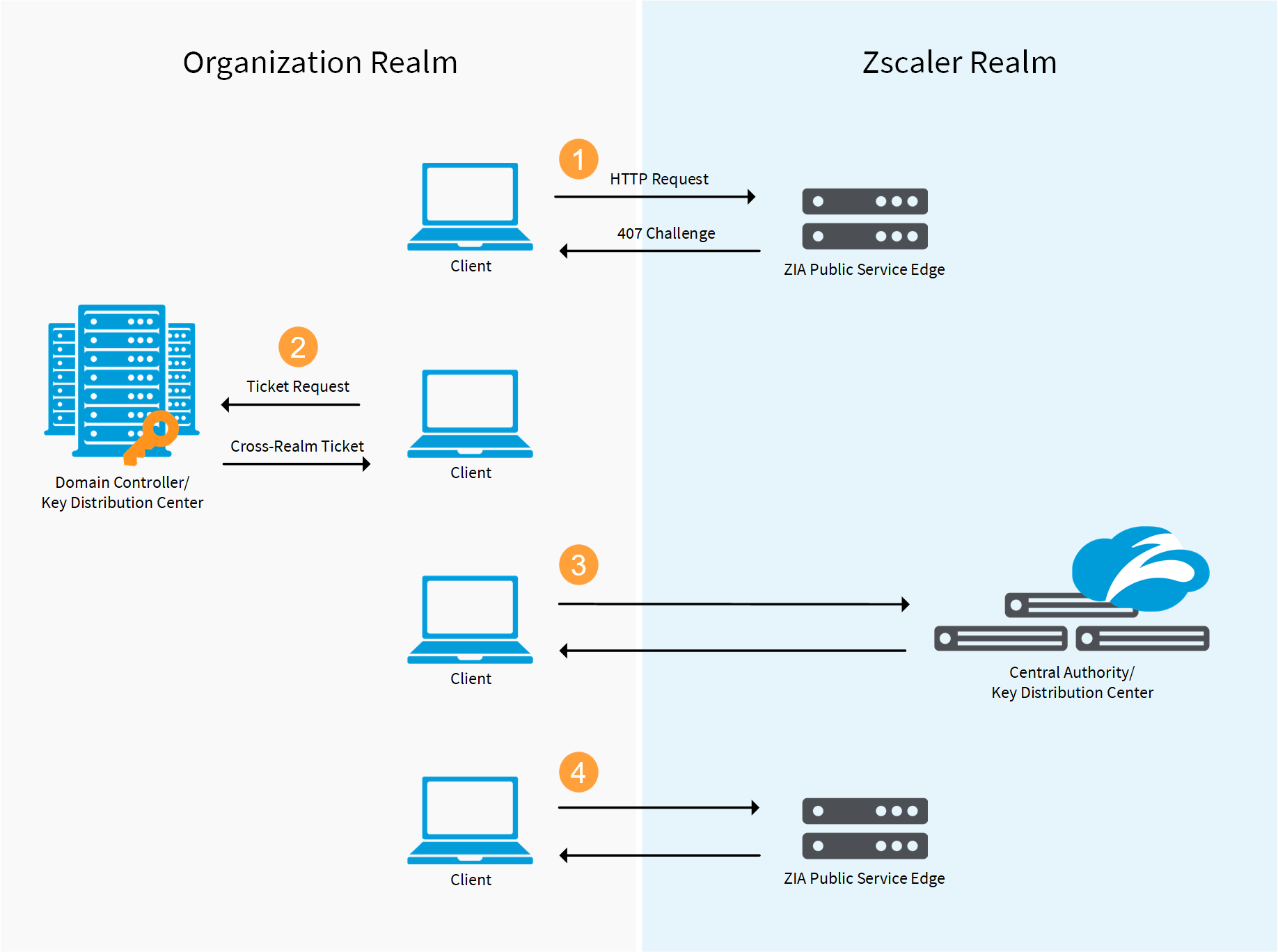
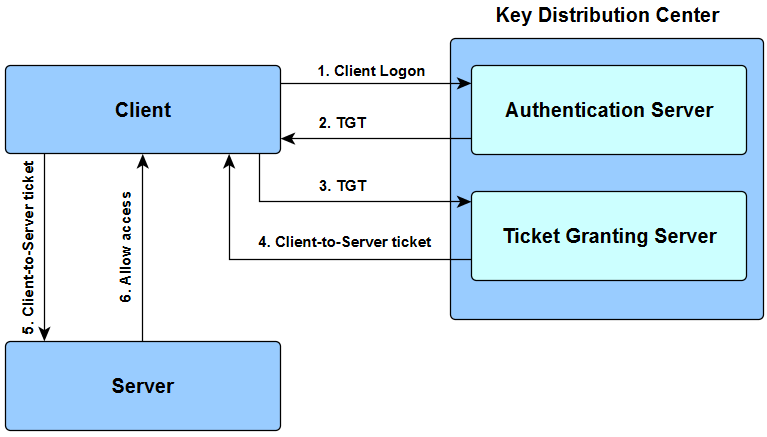
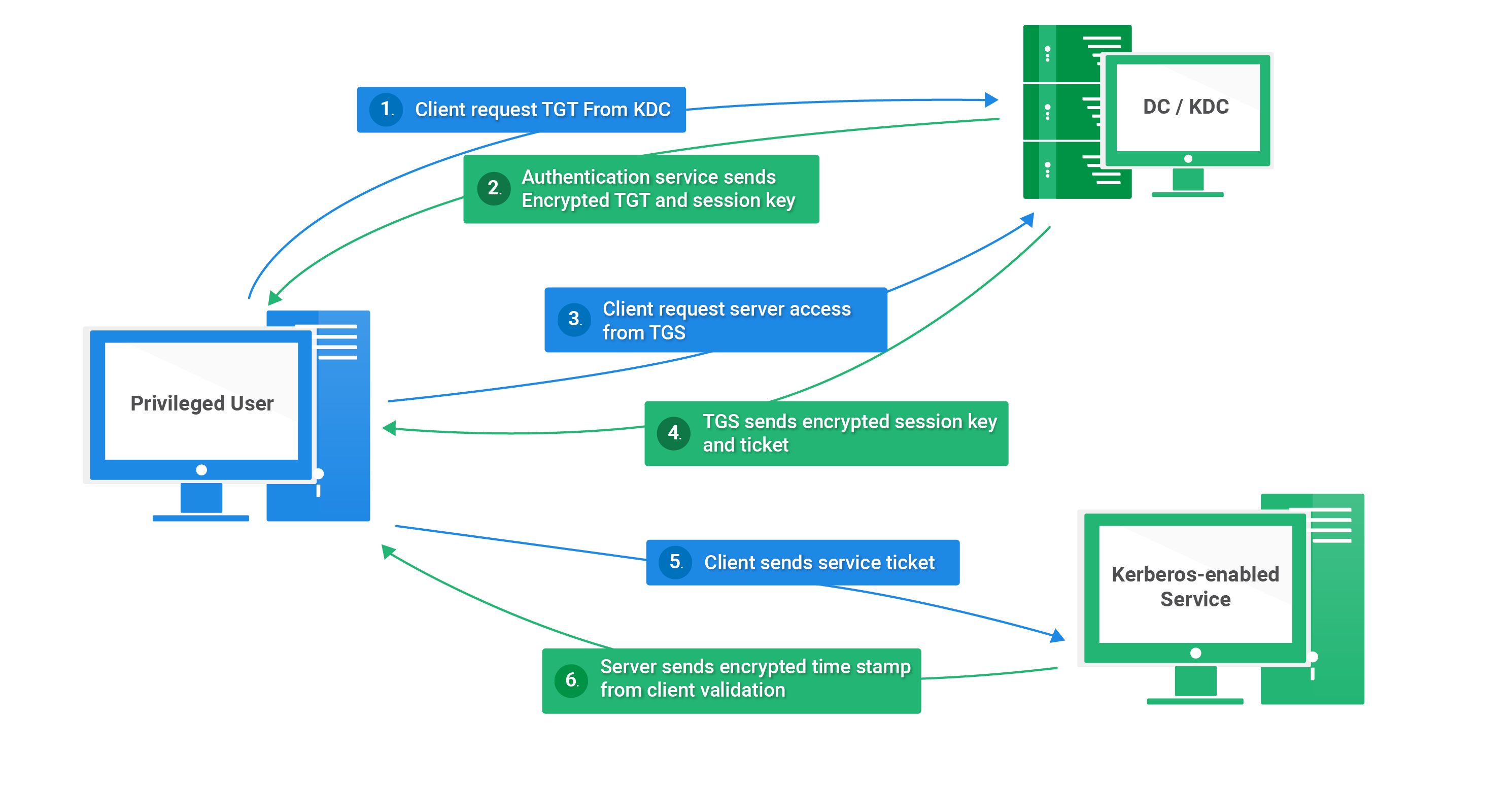
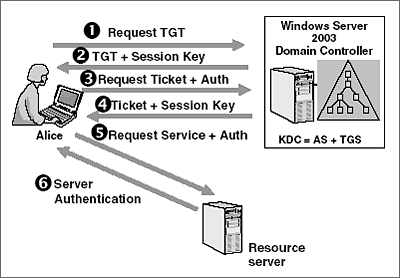
1 A simplified version of the Kerberos authentication system: both the... | Download Scientific Diagram
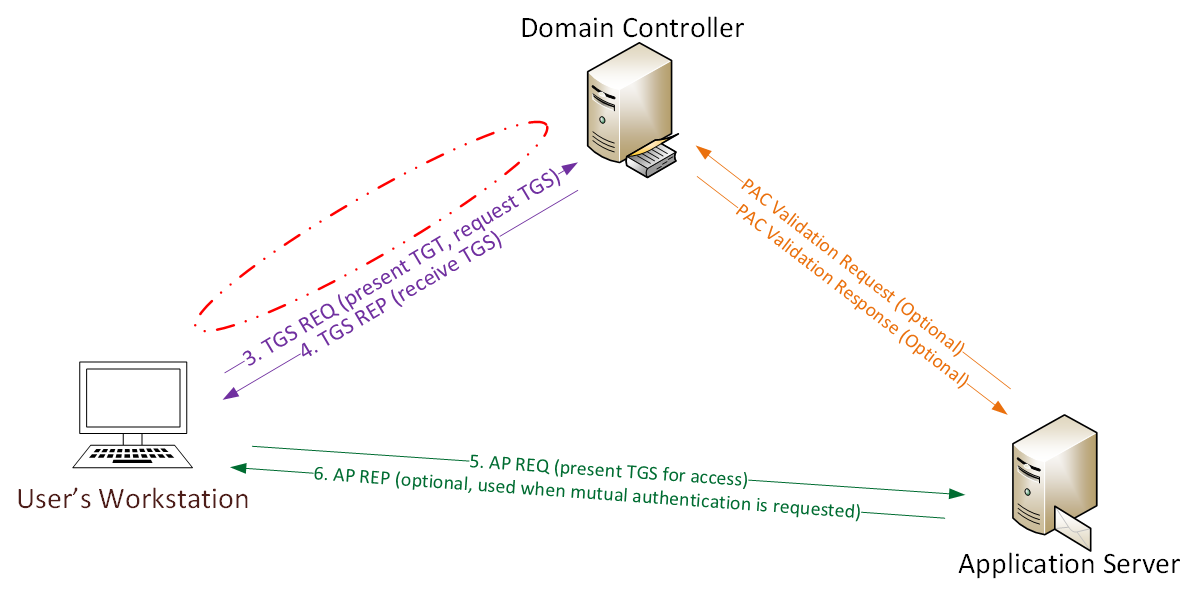
Detecting Forged Kerberos Ticket (Golden Ticket & Silver Ticket) Use in Active Directory – Active Directory Security
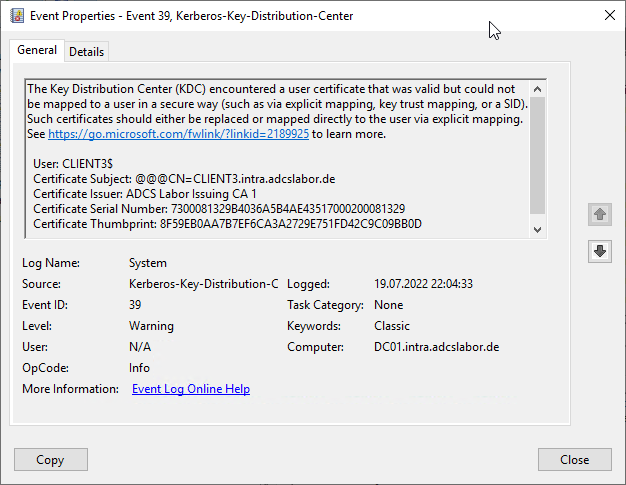
Details zum Ereignis mit ID 39 der Quelle Microsoft-Windows-Kerberos-Key-Distribution-Center – Uwe Gradenegger
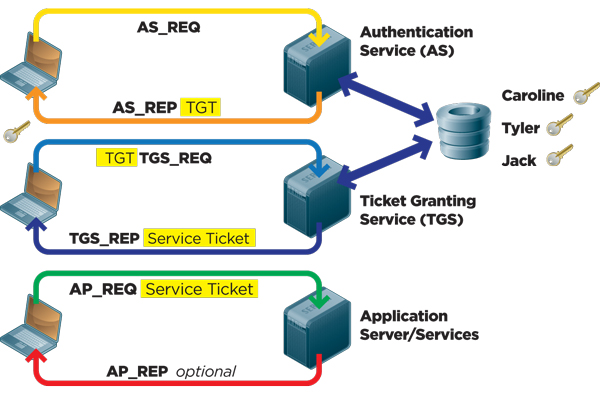
Kerberos Authentication 101: Understanding the Essentials of the Kerberos Security Protocol -- Redmondmag.com
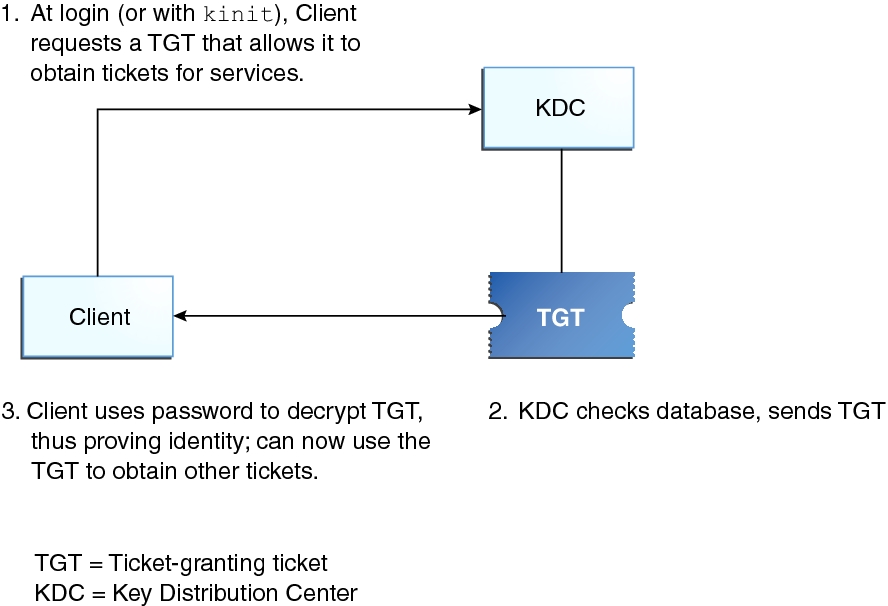
How the Kerberos Service Works - Managing Kerberos and Other Authentication Services in Oracle® Solaris 11.3