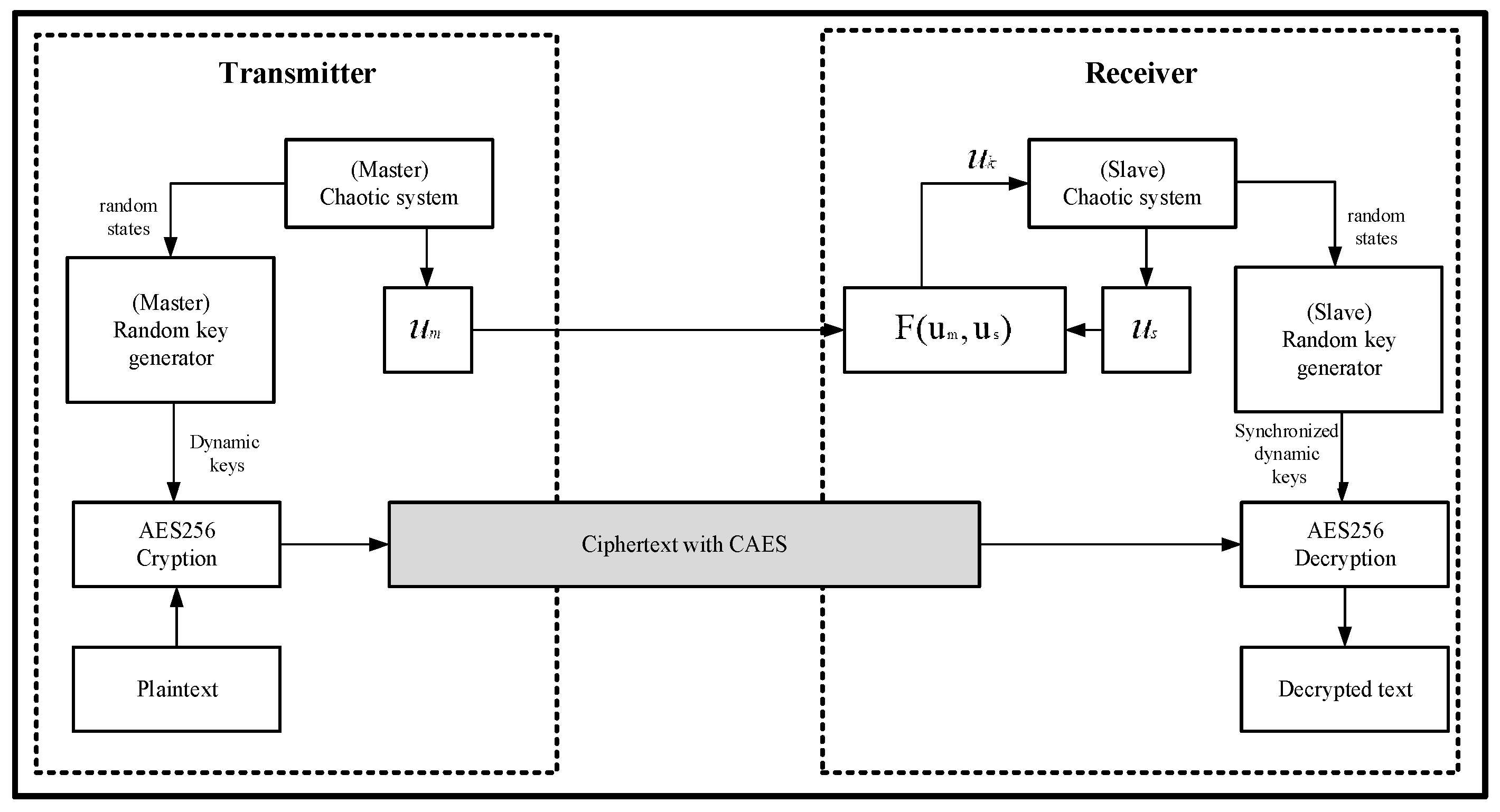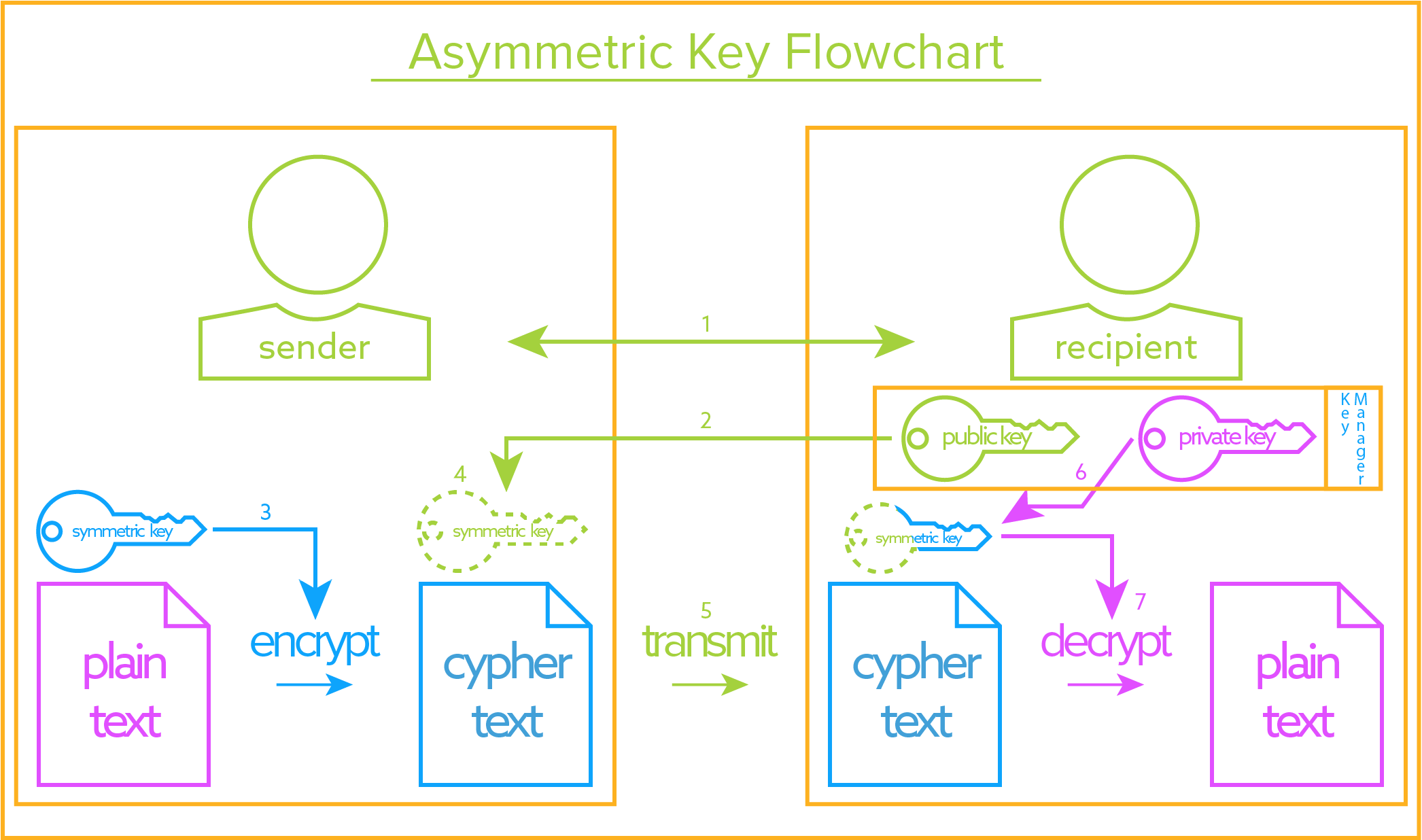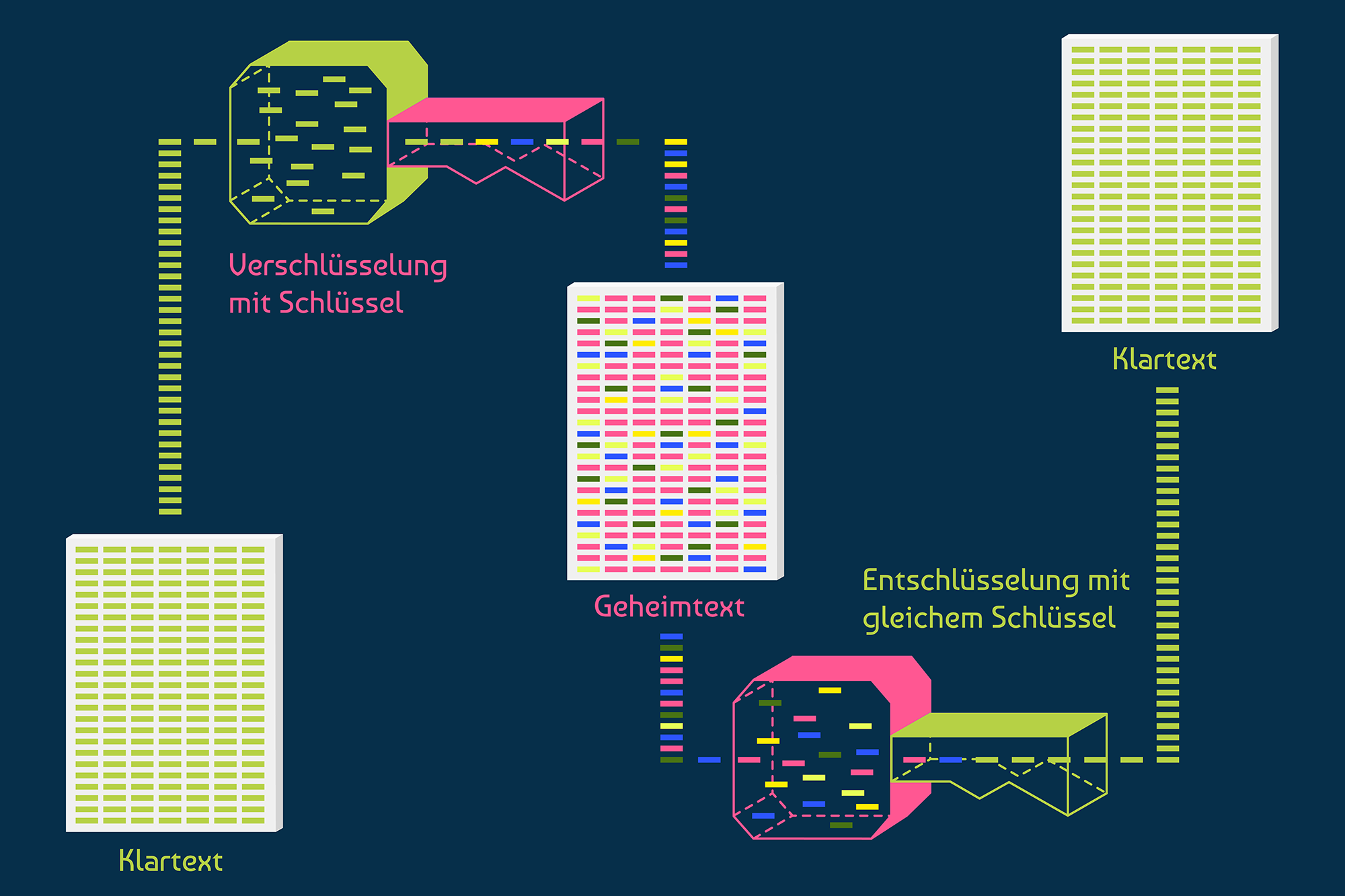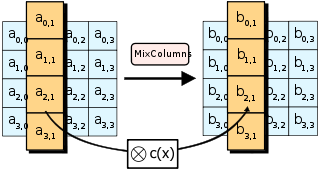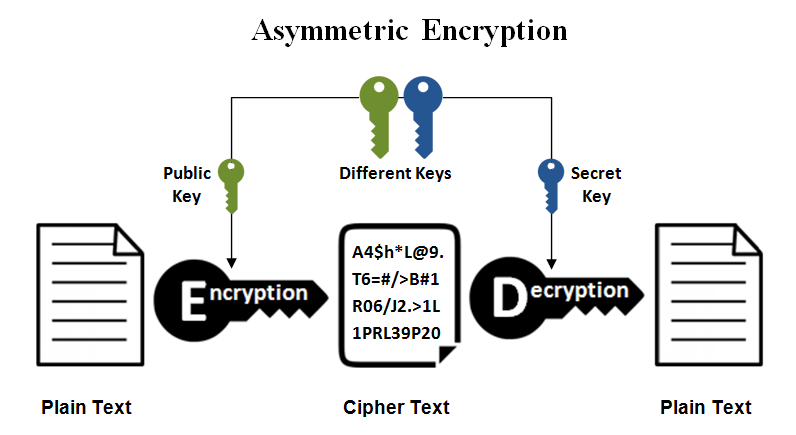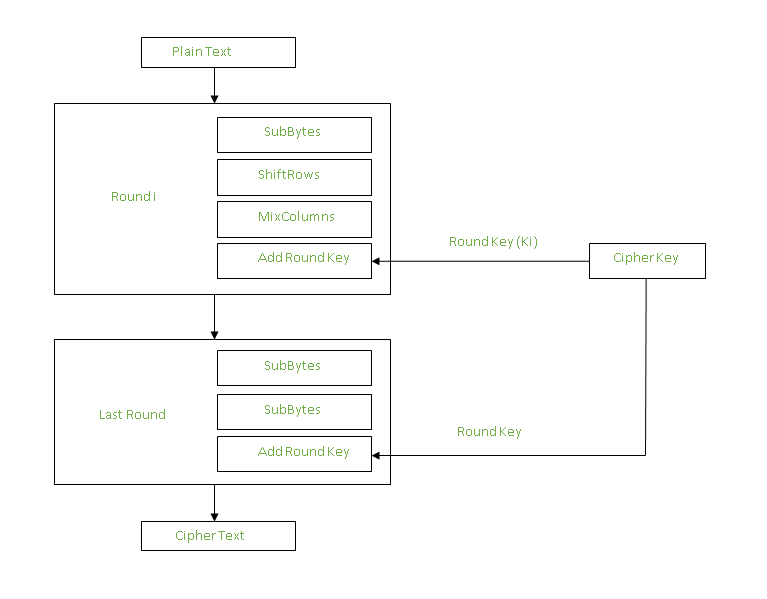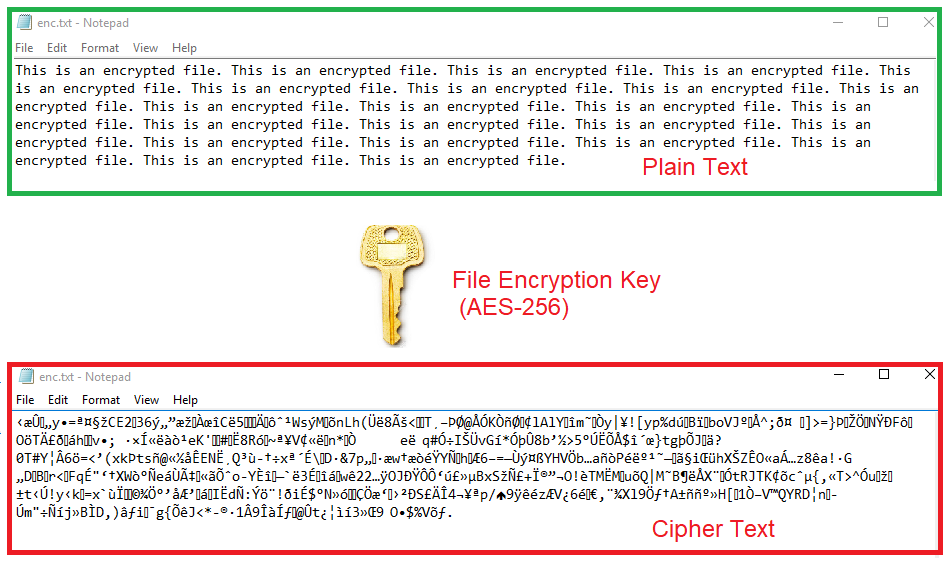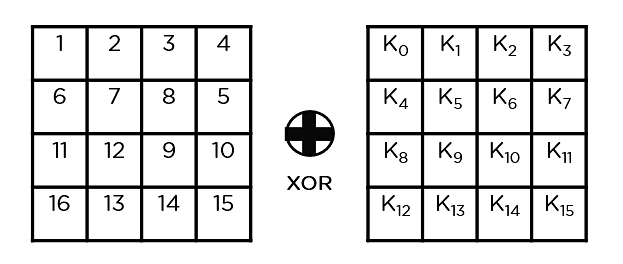
Sensors | Free Full-Text | A Dynamic Four-Step Data Security Model for Data in Cloud Computing Based on Cryptography and Steganography
![cryptanalysis - S-AES RC[i] Generation. Can someone explain how to generate the RC[i]s for these two problems I have? - Cryptography Stack Exchange cryptanalysis - S-AES RC[i] Generation. Can someone explain how to generate the RC[i]s for these two problems I have? - Cryptography Stack Exchange](https://i.stack.imgur.com/lKNyR.jpg)
cryptanalysis - S-AES RC[i] Generation. Can someone explain how to generate the RC[i]s for these two problems I have? - Cryptography Stack Exchange