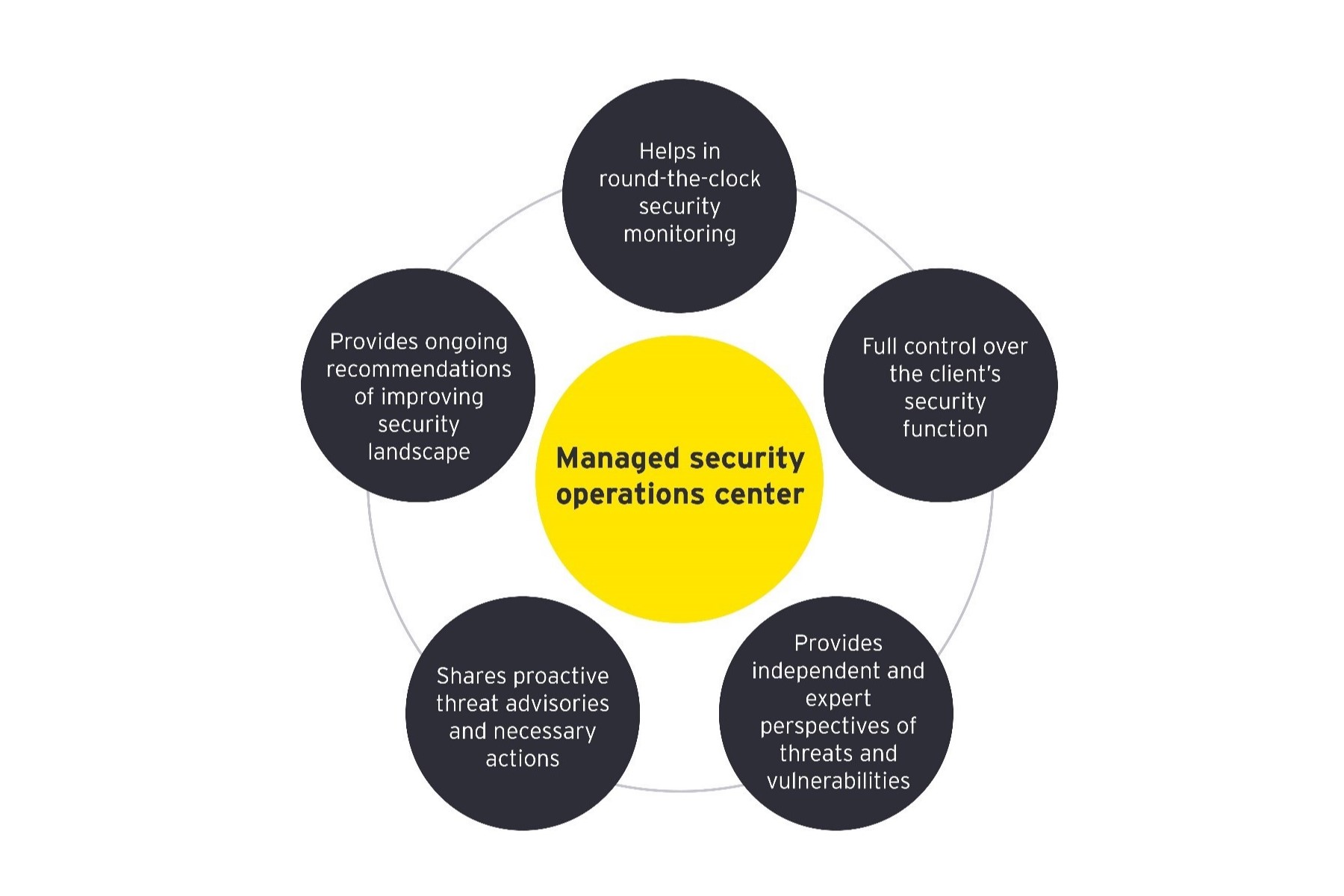
Information Security Continuous Monitoring Strategy Ppt Powerpoint Presentation Infographic Template Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
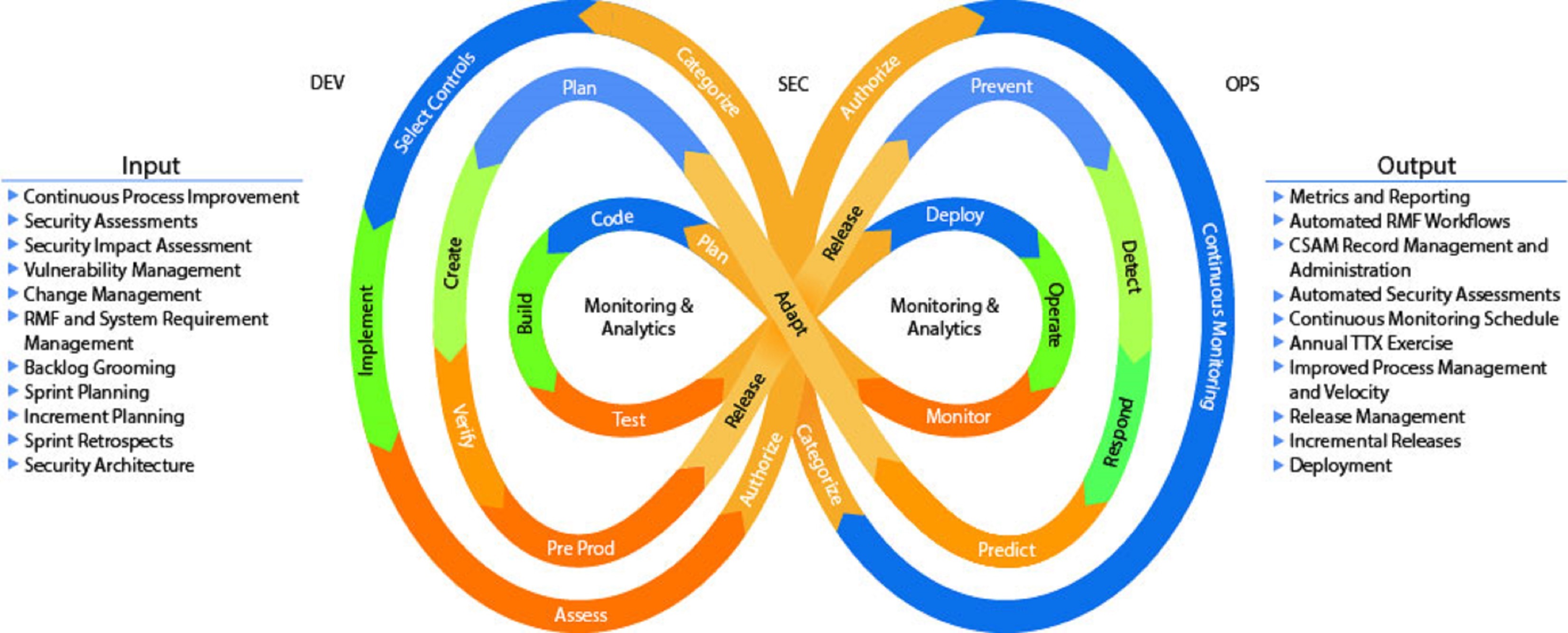
Continuous Monitoring: Keeping Your System Up to Date and Prepared for Cyberattacks – Great Government through Technology

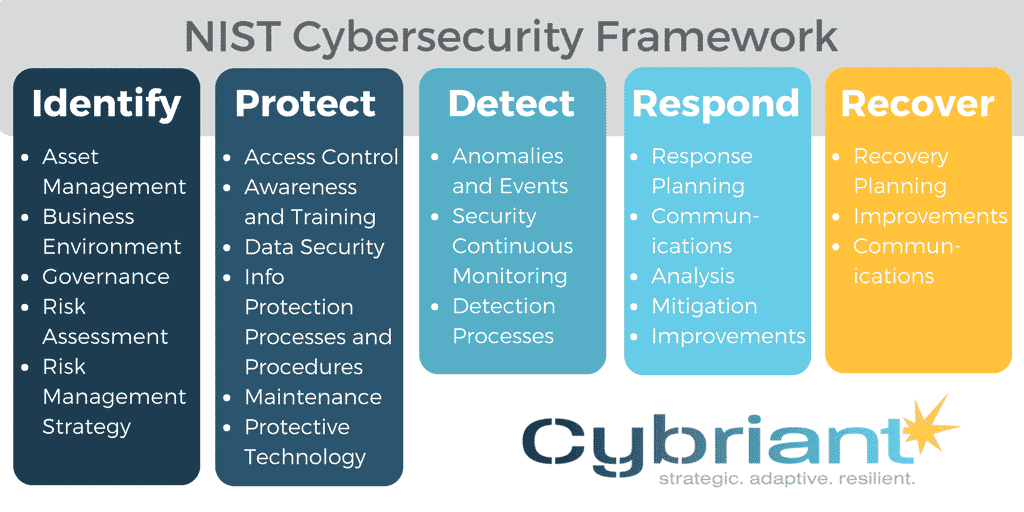
Information Security Continuous Monitoring for Federal Information Systems and Organizations | Semantic Scholar

Information Security Continuous Monitoring for Federal Information Systems and Organizations | Semantic Scholar

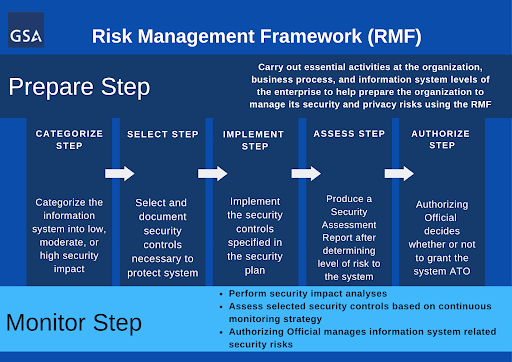
Figure 2-2 from Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations: National Institute of Standards and Technology Special Publication 800-137 | Semantic Scholar