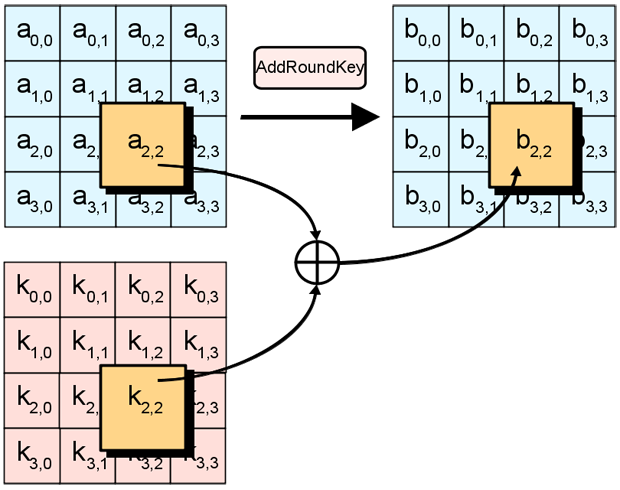
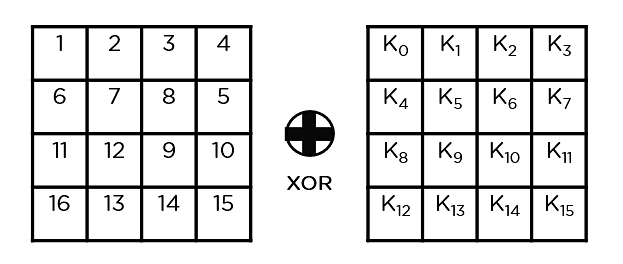
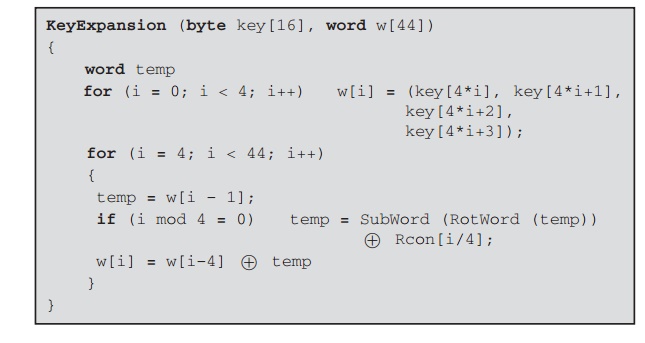
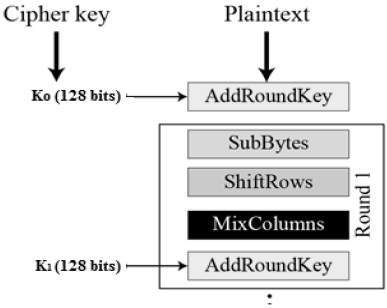
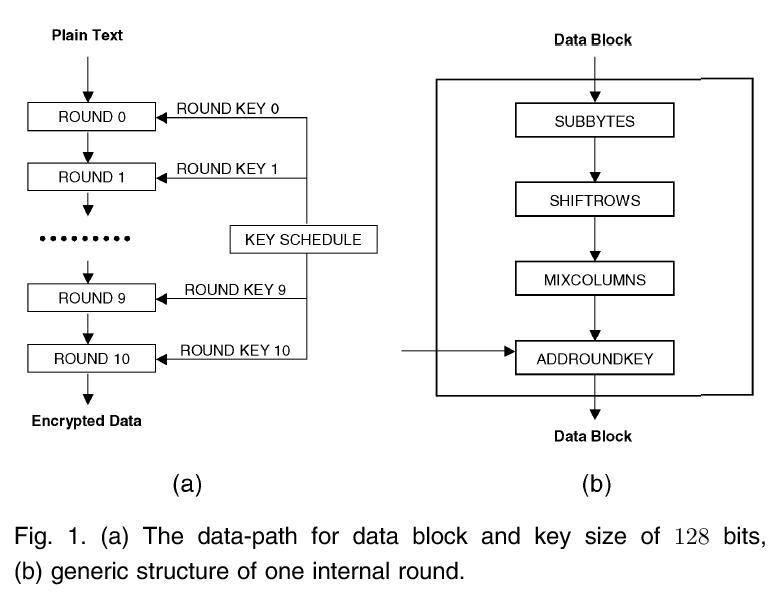
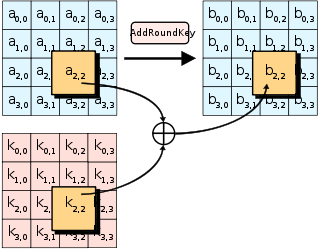
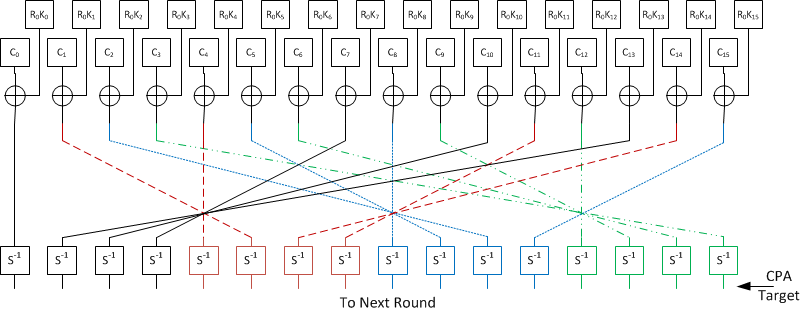
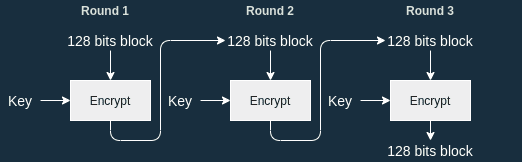
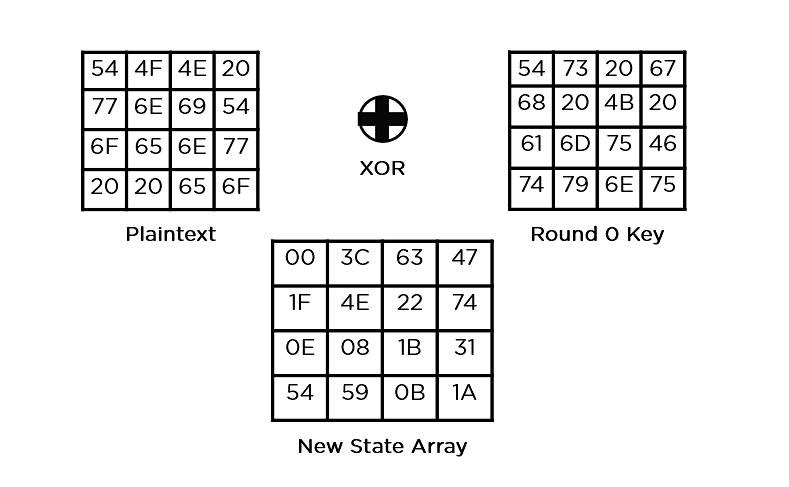
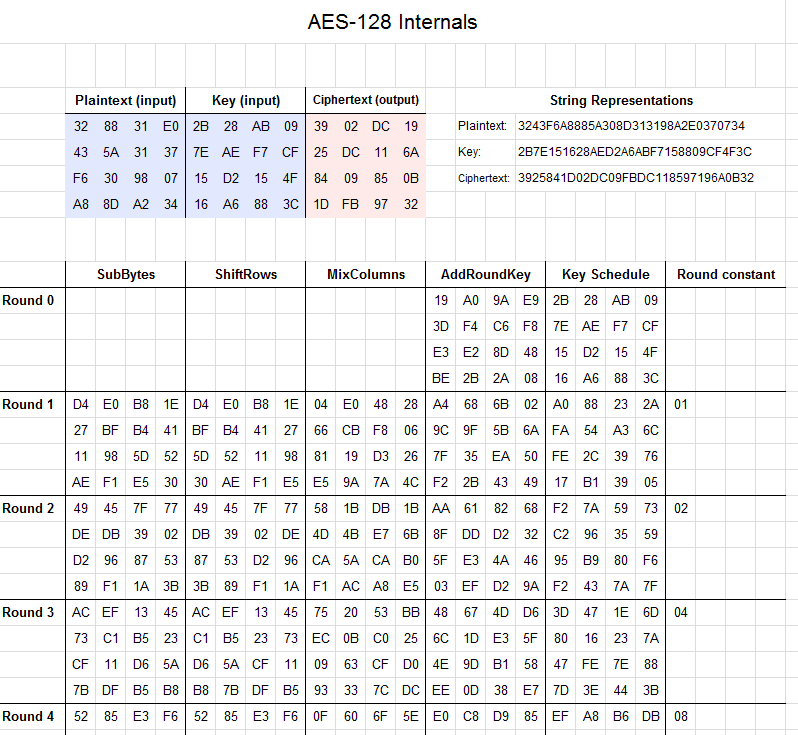
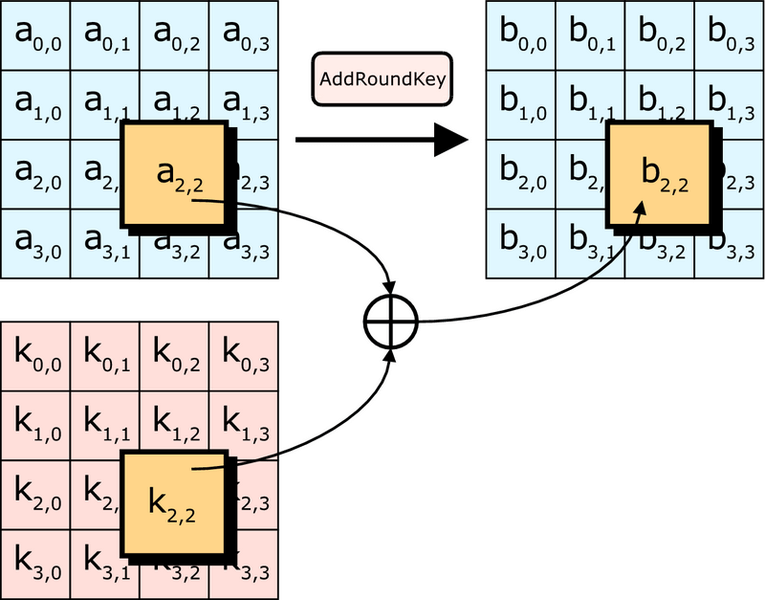
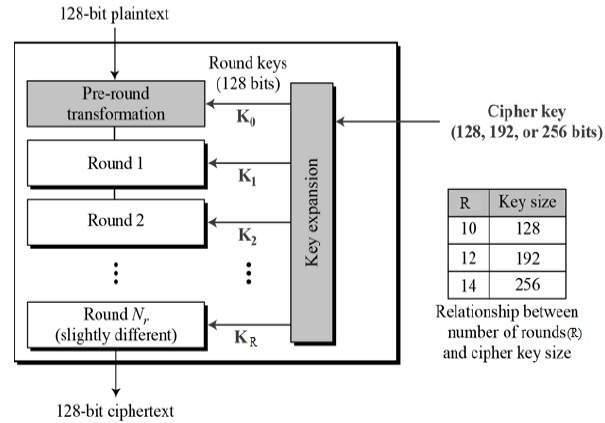
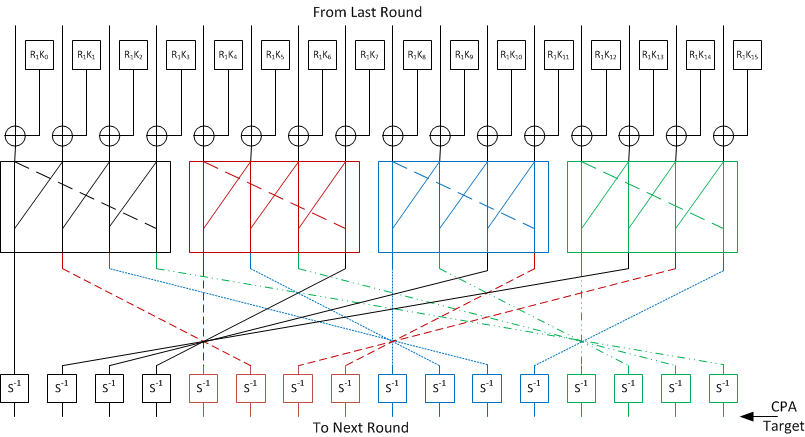
AES III - Advanced Encryption Standard - Introduction , Key Expansion in AES Cyber Security CSE4003 - YouTube

What is Advanced Encryption Standard (AES)? Definition, Encrption, Decryption, Advantages and Disadvantages - Binary Terms
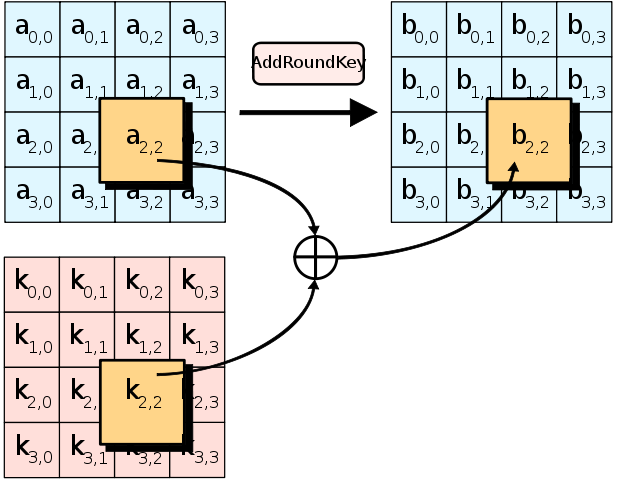
Advanced Encryption Standard (AES) - So schützen Sie Ihre sensiblen Daten einfach und verlässlich vor fremden Zugriff

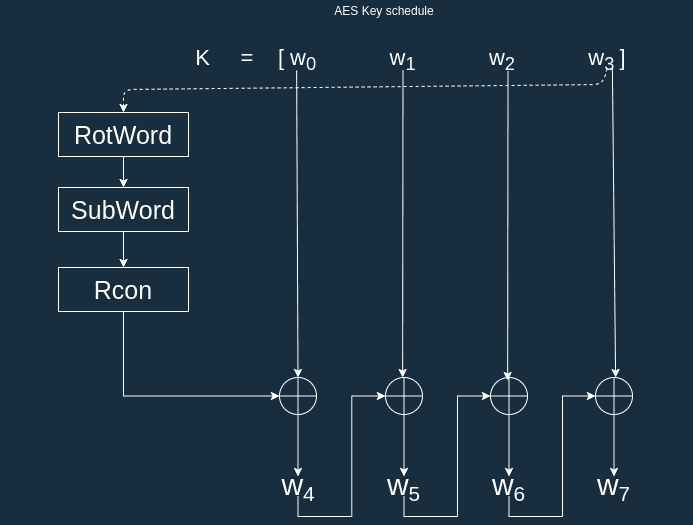
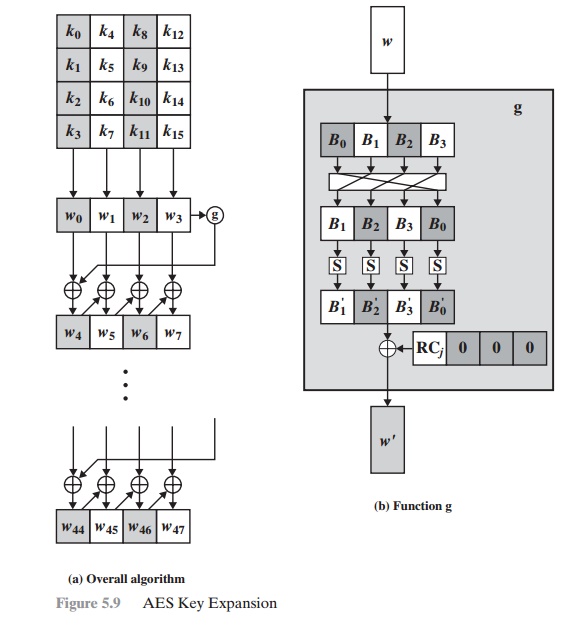
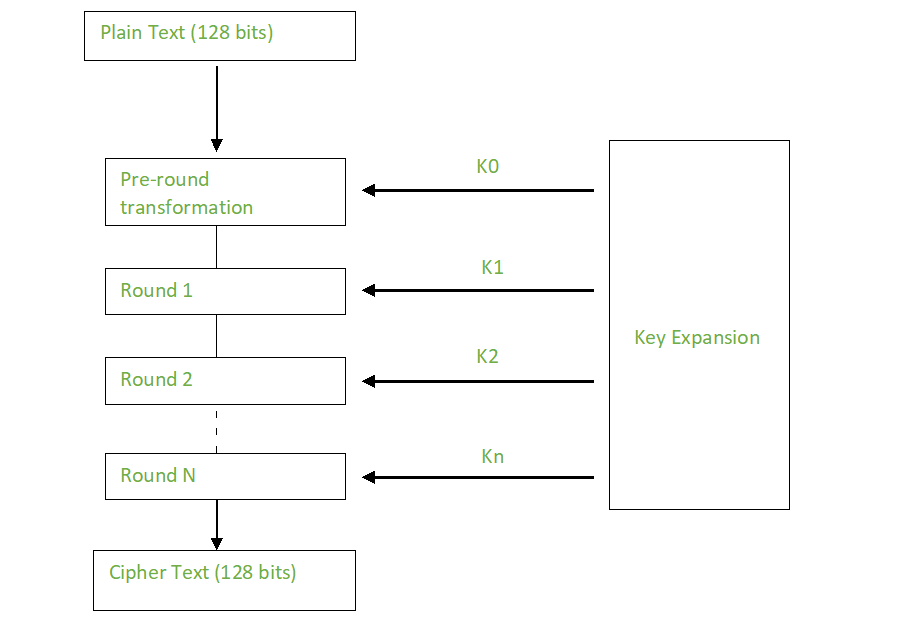
![정보보안] Advanced Encryption Standard (AES) 정보보안] Advanced Encryption Standard (AES)](https://blog.kakaocdn.net/dn/blTptN/btq5QOOc6lx/dWxiOmLBF9gpINP9Advp11/img.jpg)