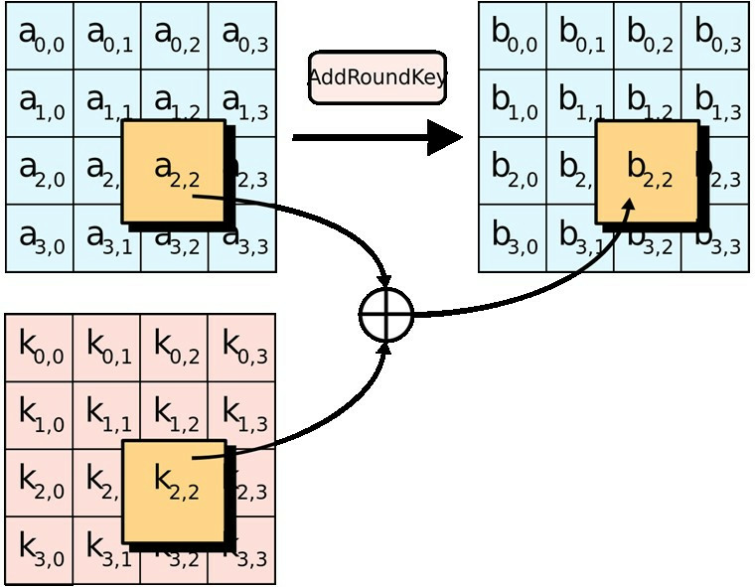
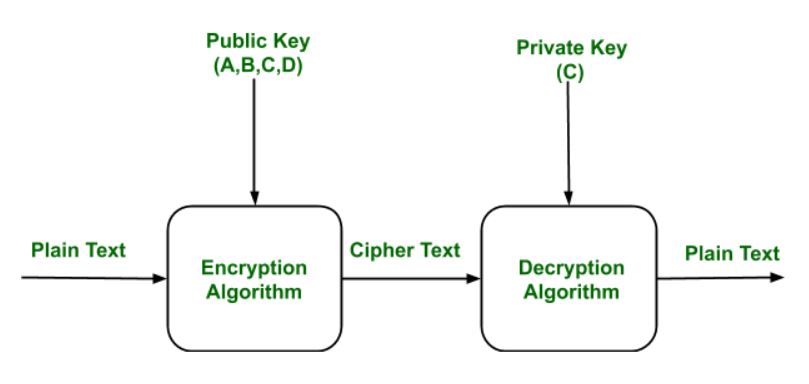
The security transmission of IPSec protocol. AES, advanced encryption... | Download Scientific Diagram

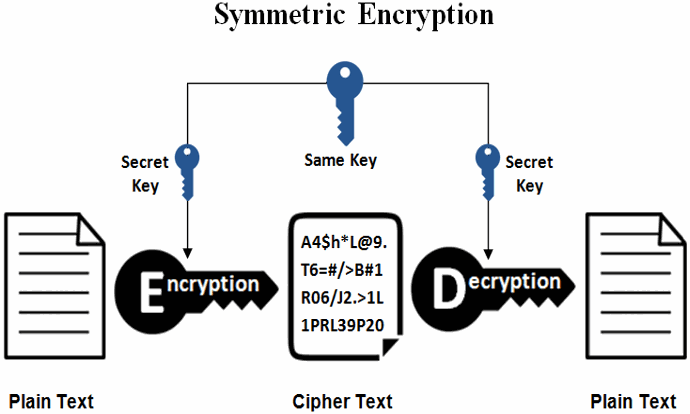
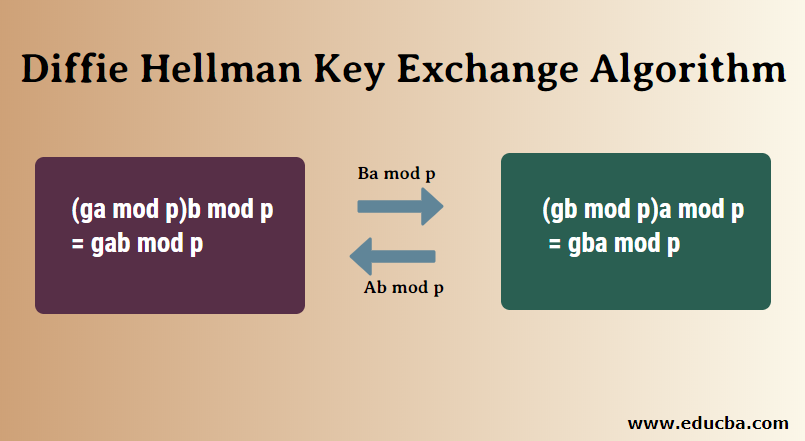
Key Management Using Combination of Diffie–Hellman Key Exchange with AES Encryption | Semantic Scholar
GitHub - Gursimratsingh/Secure-Chat-with-Implementation-of-AES-with- Diffie-Hellman-Key-Exchange: The motive of the project is to make a secure data transmission application with the help of Diffie-Hellman key exchange protocol and AES and study its ...
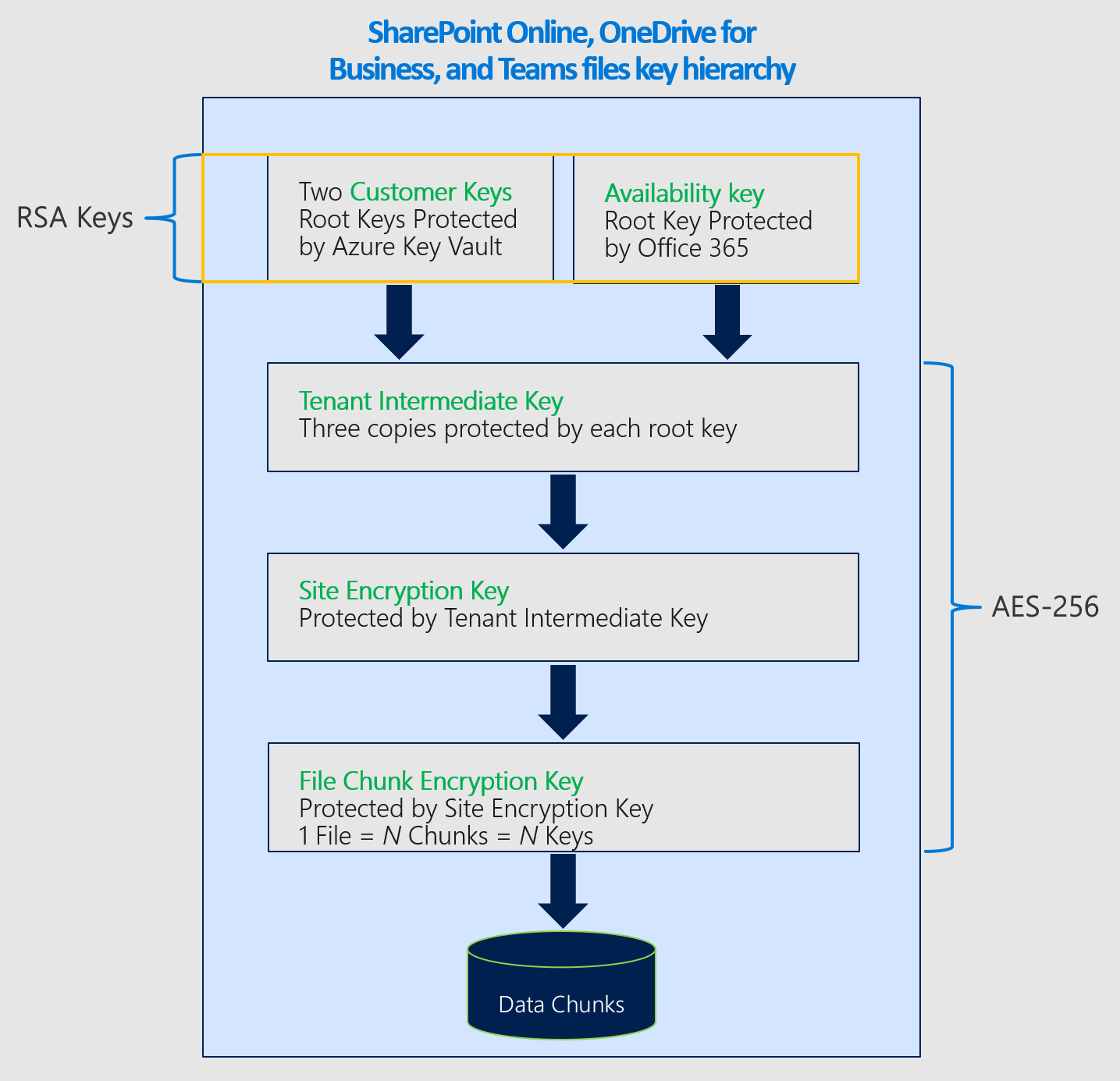
Dienstverschlüsselung mit Microsoft Purview-Kundenschlüssel - Microsoft Purview (compliance) | Microsoft Learn

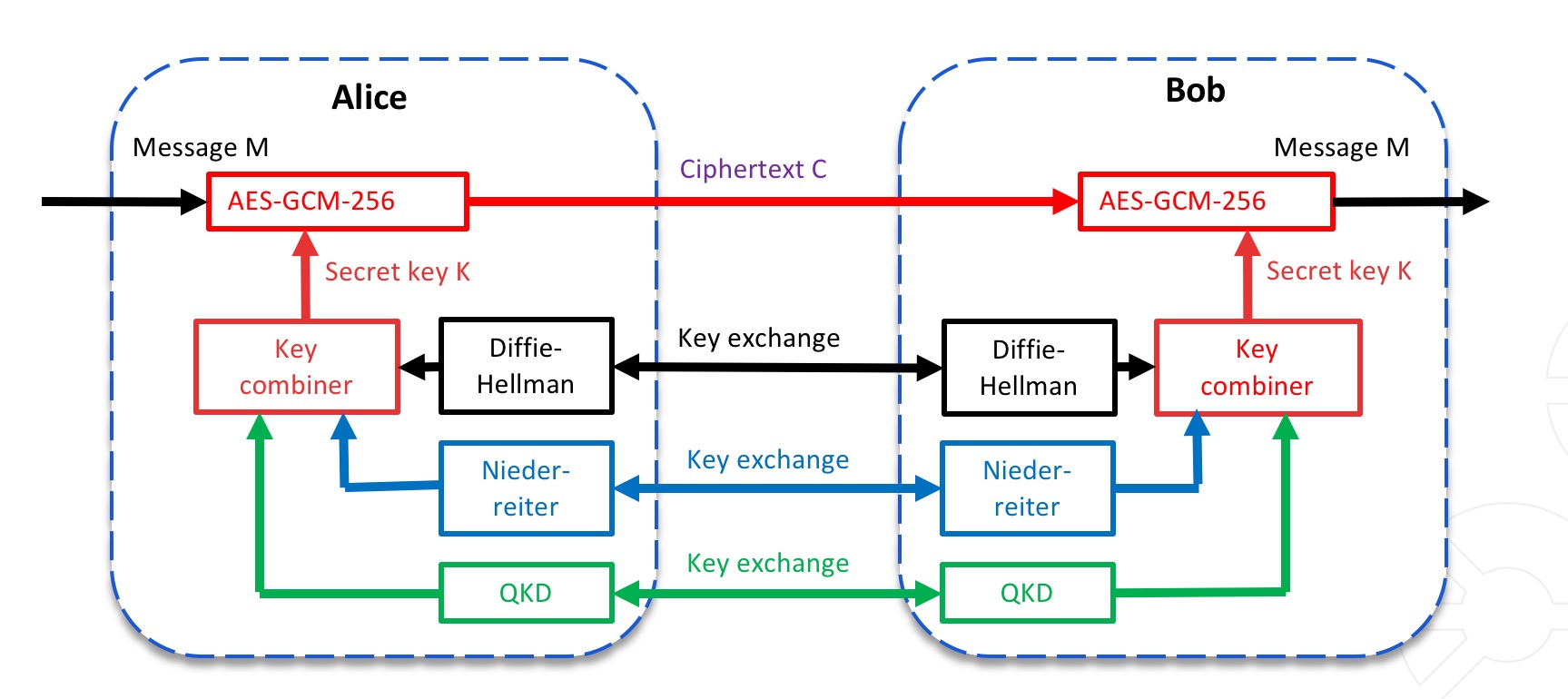
Key exchange and connection establishment. A detailed description of... | Download Scientific Diagram